Linux is an old operating system – it’s been around since 1991 – but its age hasn’t impacted its popularity. There are still 32.8 million Linux users globally, and in 2021, 27.8 million lines of code were submitted to the Linux Git repository – the largest open-source project in existance. Indeed, Linux is alive and well in the modern enterprise.
What runs on Linux? A lot:
- 2.68% of desktop PCs and laptops globally
- 23 of the top 25 websites in the world
- 96.3% of the world’s top 1 million servers
- 90% of all cloud infrastructure
- Almost all of the world’s supercomputers
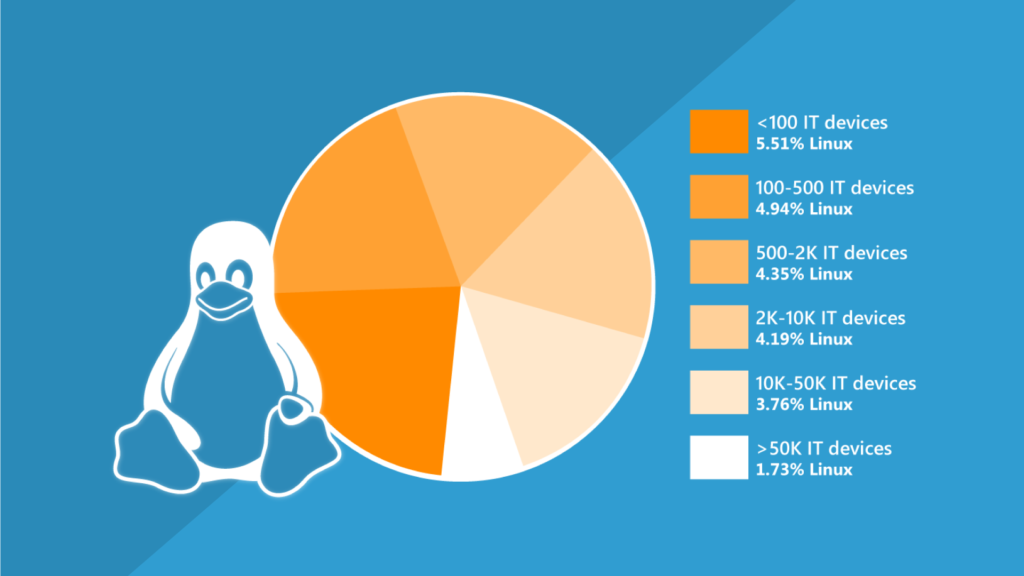
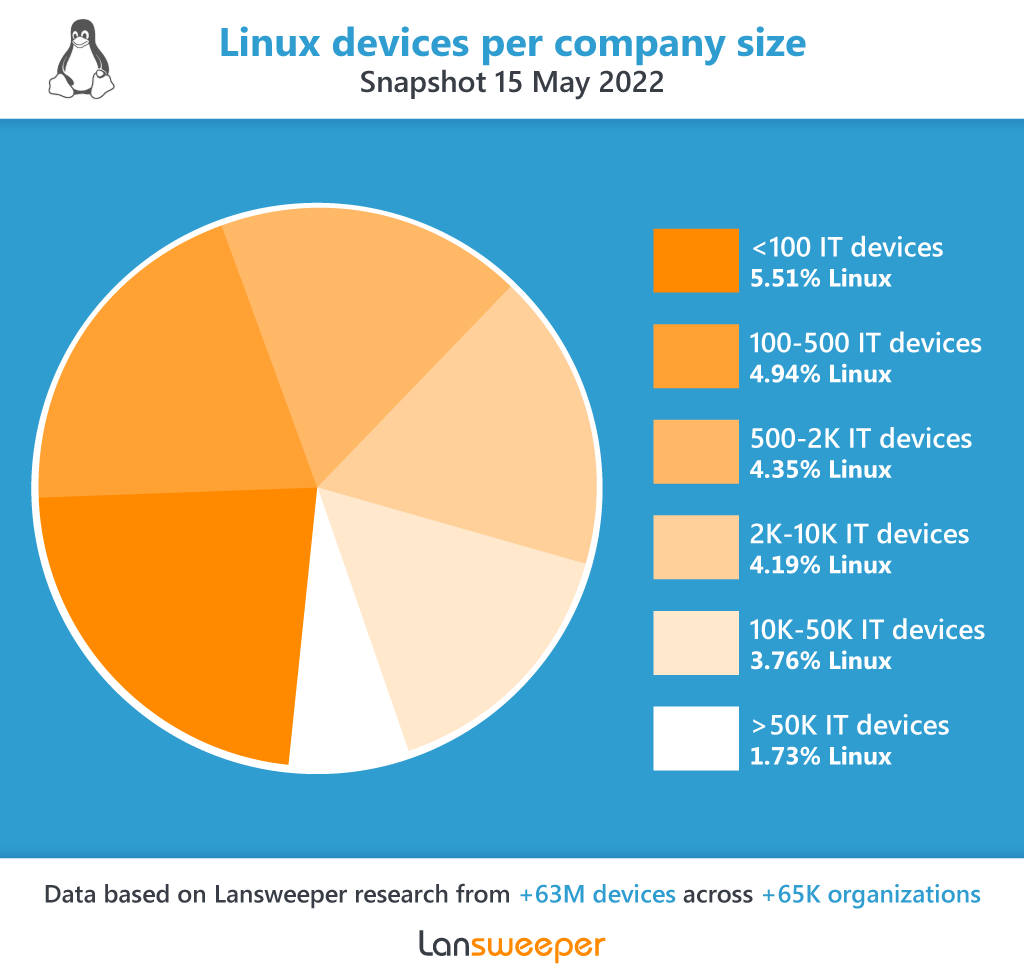
According to Lansweeper data from more than 63 million devices across over 65,000 organizations, all organizations have devices running some form of Linux (see Figure 1).
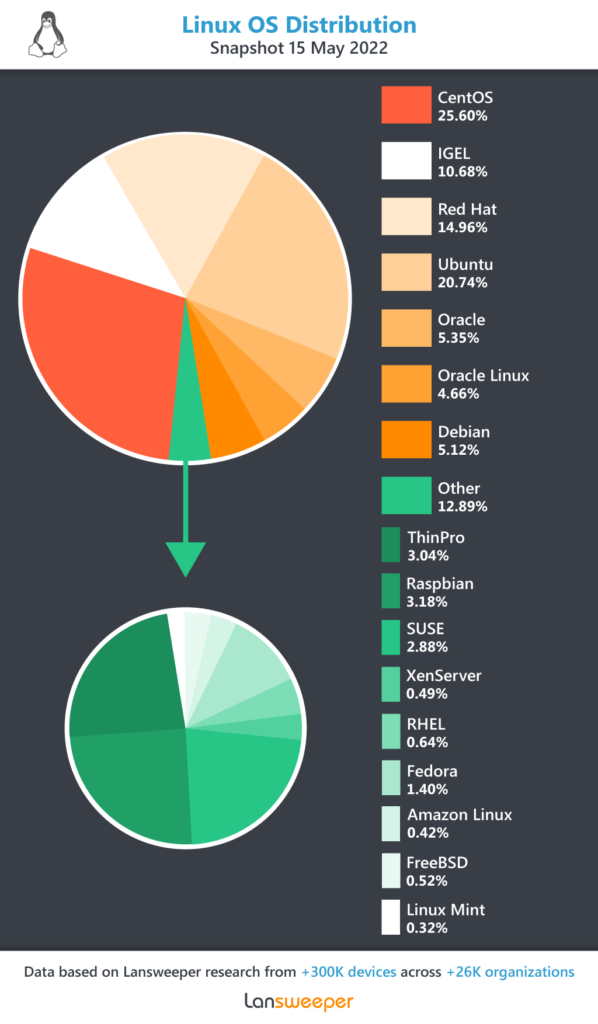
Additionally, there are many flavors of Linux in use today. Lansweeper looked at data from more than 300,000 devices acros over 26,000 organizations to determine the various types of Linux deployed and their relative popularity. By far, CentOS is the most widely used (25%) followed by Ubantu (20%) and Red Hat (15%). However, as you can see in Figure 2, there are numerous other Linux OS distributions in use today.
Most of the devices running Linux are business-critical servers, which are a desired target for cybercriminals. The larger the company grows, the more Linux devices there are that must be protected. But with so many versions and ways to install Linux, IT teams grapple with not only the complexity of tracking and managing the devices, but with keeping them secure and protected from cyber attacks. Staying on top of updates and identifying vulnerabilities that could put an organization at risk are ongoing challenges – and they’re impossible to solve using manual tracking and spreadsheets. One forgotten asset or misconfiguration could be a gateway for cybercrime.
For example, in April this year, the Microsoft 365 Defender Research Team revealed a collection of vulnerabilities dubbed Nimbuspwn that attackers can exploit to elevate privileges and gain root access to Linux desktop endpoints for the purpose of deploying malicious packages, installing ransomware, or executing malicious code. Similarly, Linux Kernel 5.8 and later are vulnerable to “Dirty Pipe”, another vulnerability that allows local users to inject and overwrite data in read-only files.
According to Microsoft, “The growing number of vulnerabilities on Linux environments emphasize the need for strong monitoring of the platform’s operating system and its components.”
Enter Lansweeper Scanning
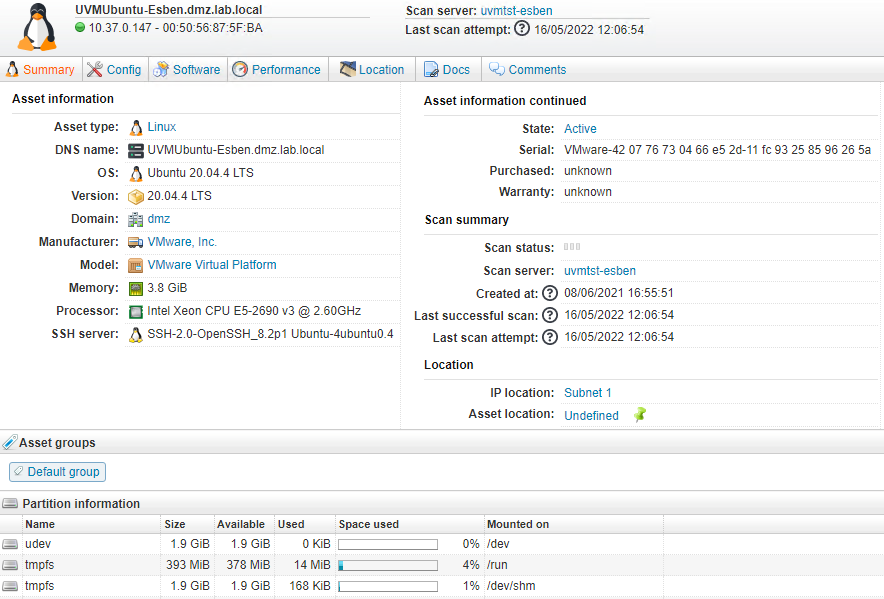
To address the growing number of Linux vulnerabilities, Lansweeper has greatly improved and extended our Linux Scanning features in our 2022 Spring release. Now users can perform deep scanning of Linux assets using a variety of methods – package manager, flatpack-lis or snap-list commands, or software in/opt;/usr/local.
We’ve significantly expanded the scope of Linux scanning, as well. In addition to an overview of the OS version, model, manufacturer, hardware details and drive information, users can now view processor data at a more granular level, categorized into general information and processor core data. Lansweeper also collects more information about the network, with tabs for Partitions, Volumes, Volume Groups, Physical Volumes and Logical Volumes.
To respond to customer demand for Linux User Scanning, Lansweeper now also automatically retrieves general user data as well as group membership information and last logged on users. File Property Scanning is also available, to collect information about the owner, type of file, file size and when the file was last accessed. Lansweeper can also remotely retrieve key resource usage data from Linux computers, like CPU & RAM usage, disk and network traffic. Finally, Lansweeper reports can be generated quickly and easily, and displayed in the dashboard to provide an overview of all Linux data.
Agent-based Scanning of Linux Devices with LsAgent
Lansweeper usually scans your entire IT environment completely Agentless. However, with networks becoming increasingly mobile and complicated, certain assets become harder to reach. Think for example of laptops out on the road, devices at remote locations or machines in protected zones (DMZs). LsAgent is a small, lightweight application that gathers data locally from Linux devices and sends it back to your Lansweeper installation.
Lansweeper’s enhanced Linux Scanning enables you to manage your Linux devices more efficiently by proactively identifying potential vulnerabilities, while helping to isolate and address any incidents to minimize organizational risk. Want to get started? You can find more information on how to setup scanning for Linux devices here.
As a bonus tip: Lansweeper’s IT team has also documented how to scan Linux systems by providing it with specific permissions, and tested it across multiple Linux distributions. Check out this ProTip by Esben to learn about Least Privilege Linux Scanning.