Ever since the boom of ransomware in 2011, reports of companies getting infected have become a regular occurrence. Especially after WannaCry in 2017 which reportedly was able to attack 200,000 victims around the globe and put ransomware safely in the #1 spot of security concerns for companies. Now there are attackers who misuse a QNAP vulnerability by remotely encrypting files on QNAP devices with 7zip. It’s a QNAP ransomware operation dubbed Qlocker.
The Boom of Ransomware
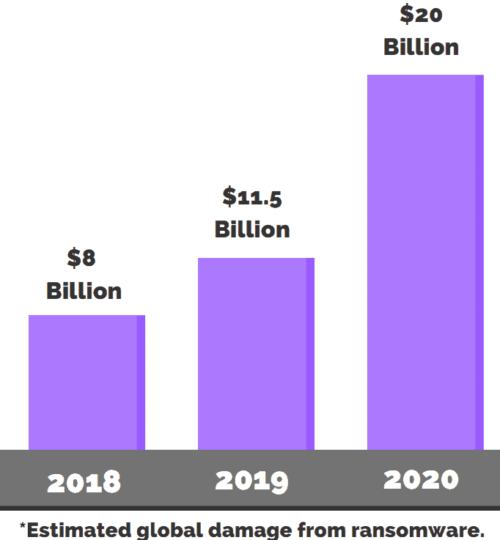
Since 2017 ransomware attacks have only been increasing, according to Purplesec, ransomware attacks grew by 350% in 2018 alone and have continued to be the most used attack against organizations. In total, the estimated cost to organizations in 2020 is a mind boggling 20 billion dollars!
Just like viruses, ransomware comes in all kinds of variations. However, the goal is always the same, find data, encrypt it and then ask for a ransom (hence the name). While most of them are created to target workstations and servers (specifically those juicy databases), ransomware creators are eager to exploit any vulnerabilities to get into a network. The recent QNAP NAS vulnerability is a good example of this where access could be gained using hard-coded credentials.
Protecting Against Ransomware
The best method to protect against ransomware is unfortunately not something only you can do by yourself:
- Keep your programs and systems up-to-date
- Do not click on unsafe links
- Do not provide personal information to unknown sources
- Do not open suspicious email attachments
- Do not use unknown USB sticks
- Only use trustworthy download sources
- Use your VPN on public networks
What is in your control is ensuring that you have an inventory of your network along with the information you need to protect your devices.
Get Started with Lansweeper
Discover assets you don’t even know about and learn why Lansweeper is used by thousands of organizations worldwide.
TRY NOWIdentifying Your Weak Spots
Let’s take the example of our QNAP NAS devices, users cannot really cause this one, so it does come down to making sure you know how many NAS devices you have, where they are, and what version they are running, etc.
Simply by installing Lansweeper the Credential-free Device Recognition will start detecting and recognizing devices that are reachable from the installation machine. This means that any NAS devices in the same subnet will already be automatically discovered.
Additionally, in the first-run wizard, your subnet will also be recommended as an initial IP-Range scanning target. You can also add additional IP Range scanning targets to discover devices on your other subnets. Something worth doing if you want a complete overview.
Now that we have the basics down, and we have scanned all our subnets. We should already have a sense of the types of devices are available in our network.
By taking a look at the asset tab, we can view all of the NAS assets. In this case, you can protect yourself against the QNAP ransomware.
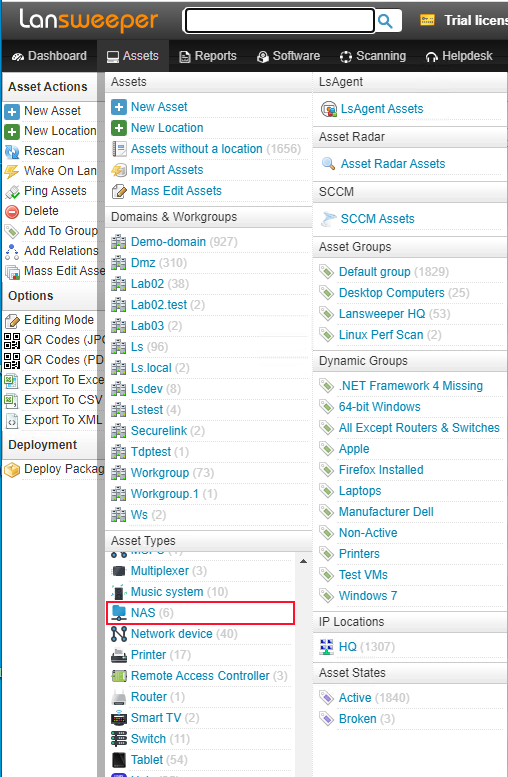
Getting the Details
To retrieve all the details, there are two methods most commonly used for NAS devices. The most common method is using SNMP. By default, Lansweeper will already have attempted to scan using SNMP by using the default “public” credential. If you have other methods of authentication, you can easily set up additional SNMP scanning to get all the details.
Lansweeper’s default SNMP scan will retrieve the basic asset details from your device. However, if you’re looking for something specific, you can go further with Custom OID Scanning. Custom OID Scanning allows you to use the manufacturer’s MIB file to choose from all the data available on the NAS.
For QNAP NAS you should be able to find the MIB file by doing the following:
- Go to Control Panel > Network & File Services > SNMP.
- Under SNMP MIB, click Download.
If you’re looking for other manufacturer’s instructions, a quick google will do. Once you have the MIB File(s), you can import & configure the scanning.
The second method that can be used is SSH scanning. This method is not always successful as it relies on the NAS device to be able to use the commands designed for Linux and Unix devices, but it can at times provide more details than SNMP. Lansweeper can help you with your cyber security.
Having an Overview
Now that we have all our QNAP NAS devices scanned, we have retrieved all the data we want. How do we get a good overview? This is where reporting comes in.
Lansweeper lets you report on any data we collect regarding the QNAP vulnerability. To help you get started, our experts created a report which shows you all NAS devices that have their manufacturer as QNAP. Additionally, if you have scanned custom OID data, it will also be shown.
Did you already read our blog regarding the dangers of malvertising? Have a look and run our custom report.