Mitigating Cybersecurity Risks Through Effective Vulnerability Assessment
Contents
Vulnerability assessments are a cornerstone of any strong cybersecurity strategy. They provide the insight needed to uncover weaknesses before attackers can exploit them, helping organizations reduce risk and strengthen resilience. In this post, we’ll explore why vulnerability assessments are so critical and share best practices for making them an integral part of your cybersecurity risk management approach.
Closing the Gaps With Automated Vulnerability Management
Why visibility is your first — and most critical — line of defense.
Download the White PaperWhat Is a Vulnerability Assessment?
A vulnerability assessment is essentially a thorough check-up for your IT environment. It systematically examines networks, systems, and applications to uncover security weaknesses, such as outdated software, incorrect configurations, or obsolete security protocols, that could be exploited by malicious actors.
The goal is straightforward: detect and address vulnerabilities before they lead to harm. Beyond identifying potential risks, a well-executed assessment provides clear, actionable guidance to strengthen defenses and reduce the likelihood of costly security incidents.
How Does Vulnerability Assessment Mitigate Cybersecurity Risks?
Research from the Ponemon Institute shows that 60% of organizations have suffered data breaches that could have been avoided by patching known vulnerabilities. This highlights why vulnerability assessments are essential in modern cybersecurity.
By systematically identifying and ranking security weaknesses, these assessments give you the insight you need to take action before attackers can exploit them. Addressing issues, such as outdated software, misconfigurations, or insecure settings, early on dramatically lowers the risk of a successful cyberattack.
Why Are Vulnerability Assessments Critical for Organizations?
Vulnerability assessments are critical because they provide you with a clear understanding of your security posture and help prioritize remediation efforts based on risk severity. Thanks to these proactive assessments you can address security gaps before attackers can exploit them, significantly reducing the likelihood of successful cyberattacks.
For example, a vulnerability assessment might reveal that a critical business application is running outdated software with known exploits, allowing you to patch this high-risk vulnerability immediately.
According to the National Institute of Standards and Technology (NIST), organizations that regularly conduct vulnerability assessments can significantly reduce their attack surface and lower the risk of data breaches.
Key benefits include:
- Proactive risk identification before exploitation occurs
- Improved compliance with industry standards and regulations
- Enhanced resilience against evolving cyber threats
- Cost reduction by preventing expensive security incidents
How Does Vulnerability Assessment Help in Mitigating Cybersecurity Risks?
Regular vulnerability assessments mitigate cybersecurity risks by providing continuous visibility into security weaknesses and enabling prioritized remediation based on threat severity and business impact. This systematic approach ensures that the most dangerous vulnerabilities are addressed first, optimizing resource allocation in security-constrained environments.
The mitigation process works through:
- Continuous monitoring for new vulnerabilities as systems and threats evolve
- Risk-based prioritization categorizing threats by severity, impact, and exploitability
- Proactive remediation addressing critical issues before they can be exploited
- Compliance support helping organizations meet regulatory requirements and avoid fines
What Are the Key Steps in Conducting an Effective Vulnerability Assessment?
An effective vulnerability assessment involves three critical steps: asset identification, systematic scanning, and risk-based prioritization. Following this structured approach ensures comprehensive coverage and efficient resource allocation.
Step 1: How Do You Identify Potential Vulnerabilities?
Start by creating a comprehensive inventory of all IT assets, including hardware, software, and network components to set the stage for a more focused assessment. This foundational step involves reviewing known security issues that could be exploited buy attackers such as:
- Outdated software versions
- System misconfigurations
- Exposed services and open ports
- Default or weak credentials
- Unpatched security flaws
Step 2: How Do You Scan and Assess System Vulnerabilities?
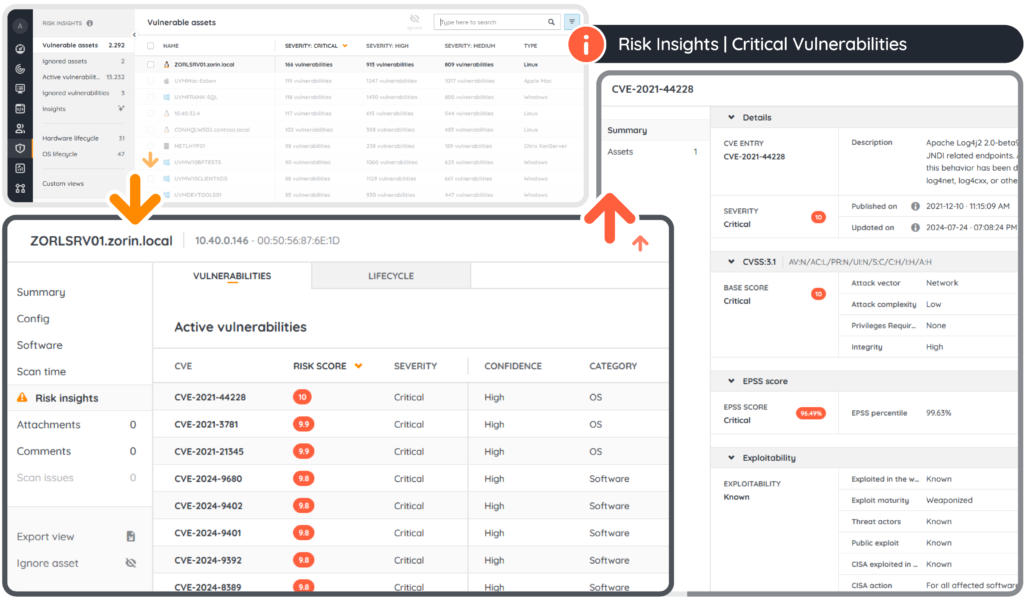
Use automated vulnerability scanning tools to systematically examine networks, systems, and applications for known security weaknesses. Tools like Lansweeper’s Risk Insights provide detailed reports that help assess the nature and severity of identified vulnerabilities.
The scanning and assessment process should cover:
- Network infrastructure components
- Operating systems and applications
- Web applications and databases
- Cloud services and configurations
- Mobile devices and endpoints
- The relationships between all of these
Step 3: How Do You Prioritize Vulnerabilities for Remediation?
Prioritize vulnerabilities based on three key factors: severity level, potential business impact, and exploitability in your environment. Focus first on high-priority vulnerabilities affecting critical systems or those with known active exploits.
Use this prioritization framework:
- Critical: Immediate remediation required (0-24 hours)
- High: Address within one week
- Medium: Remediate within one month
- Low: Address during scheduled maintenance windows
This approach allows you to allocate resources effectively and address the most dangerous vulnerabilities first, reducing the risk of successful attacks.
Integrating Vulnerability Assessment into IT Risk Management
Vulnerability assessments help identify specific weaknesses in systems, applications, and networks that could be exploited by attackers, which are then analyzed in the context of the organization’s broader risk landscape. By linking vulnerability assessment to risk management security teams can evaluate the potential impact of each vulnerability on critical assets and operations, providing a more holistic view of the risks the organization faces.
With vulnerability assessment data on-hand, your team can:
- Prioritize vulnerabilities based on severity, exploitability, and criticality of affected assets.
- Use assessment data to focus on remediating the most critical vulnerabilities first.
- Integrate this data into risk prioritization to allocate resources effectively and address the most significant threats, reducing overall risk.
- Incorporate assessment results into incident response strategies to prepare for potential exploitation.
- Ensure response teams are aware of critical vulnerabilities and have predefined action plans.
- Streamline response processes, reduce response times, and minimize the impact of security incidents, enhancing resilience against cyber threats.
What Are the Best Practices for Vulnerability Management?
Effective vulnerability management requires implementing seven key practices that create a comprehensive security framework. These practices work together to minimize exposure windows and maintain strong security posture.
- Keeping Software and Systems Up-to-Date: How Often Should You Update Software and Systems?
Maintain up-to-date software and systems by applying security patches immediately upon release, especially for critical vulnerabilities. Establish automated patch management processes where possible to reduce human error and deployment delays. - Regularly Patch Known Vulnerabilities: What Is the Best Approach to Patch Management?
Implement a structured patch management schedule that prioritizes critical patches for high-risk vulnerabilities with known exploits. Use automated tools to identify, test, and deploy patches systematically across your environment. - Monitor and Audit System Configurations: How Do You Monitor System Configurations Effectively?
Conduct regular configuration audits to ensure all systems adhere to security best practices and organizational policies. Monitor for misconfigurations such as open ports, default passwords, or improper access controls that introduce vulnerabilities. - Perform Regular Vulnerability Scans: What Is the Optimal Frequency for Vulnerability Scans?
Perform vulnerability scans continuously or at minimum weekly for critical systems, with comprehensive monthly scans for all assets. Integrate scanning into your continuous monitoring strategy for real-time vulnerability detection. - Implement a Risk-Based Approach: How Do You Implement a Risk-Based Vulnerability Approach?
Not all vulnerabilities present the same level of risk. Prioritize vulnerabilities using a risk-based methodology that considers threat severity, asset criticality, and potential business impact. This approach optimizes resource allocation and ensures the most dangerous vulnerabilities receive immediate attention. - Leverage Threat Intelligence: How Can Threat Intelligence Enhance Vulnerability Management?
Integrate current threat landscape intelligence to understand which vulnerabilities are actively being exploited in the wild. This intelligence helps prioritize remediation efforts based on real-world threat activity rather than just theoretical risk scores. - Conduct Penetration Testing: Why Is Penetration Testing Important for Vulnerability Assessment?
Conduct regular penetration testing to actively exploit vulnerabilities in controlled environments and validate the effectiveness of security measures. This practice identifies weaknesses that automated scans might miss and provides insights into potential attack paths.
How Do You Choose the Right Vulnerability Assessment Solution?
Select a vulnerability assessment tool that provides comprehensive coverage of your IT environment while integrating seamlessly with existing security infrastructure. Consider factors like scalability, ease of use, reporting capabilities and support quality when making your decision.
Essential features to evaluate:
- Comprehensive coverage across networks, systems, applications, and cloud services
- Automated scanning with monitoring capabilities
- Risk-based reporting that prioritizes vulnerabilities effectively
- Integration capabilities with SIEM systems, firewalls, and patch management tools
- Compliance reporting and customizable dashboards for regulatory requirements
- Threat intelligence integration for enhanced decision-making
- Automated and manual testing, like penetration testing
Mitigate Risk with Lansweeper
Lansweeper helps organizations with vulnerability assessment and management by providing comprehensive visibility into their entire IT environment. It automatically discovers and inventories all hardware, software, and network assets, enabling security teams to identify vulnerabilities such as outdated software, unpatched systems, and misconfigurations.
Lansweeper’s Risk Insights gather data from the VulnCheck, CISA, and MSRC databases to discover known vulnerabilities that are a threat your network and give you a comprehensive list of at-risk assets so you can take immediate action.
By integrating with various security tools and offering detailed reporting and analysis, Lansweeper streamlines the process of prioritizing and remediating vulnerabilities based on risk levels, ensuring a proactive approach to cybersecurity.
See Lansweeper in Action – Watch Our Demo Video
Sit back and dive into the Lansweeper interface & core capabilities to learn how Lansweeper can help your team thrive.
WATCH DEMOFAQ
-
What is the difference between vulnerability assessment and penetration testing?
Vulnerability assessment identifies and catalogs security weaknesses, while penetration testing actively exploits these vulnerabilities to demonstrate potential impact. Vulnerability assessments provide broad coverage for ongoing monitoring, whereas penetration testing offers deep, targeted analysis of specific attack scenarios.
-
How often should organizations conduct vulnerability assessments?
Organizations should perform continuous vulnerability scanning with formal assessments conducted monthly or quarterly depending on their risk profile. High-risk environments or those handling sensitive data may require more frequent assessments.
-
What are the most common vulnerabilities found in assessments?
The most commonly identified vulnerabilities include unpatched software, misconfigurations, weak authentication mechanisms, and exposed services. According to industry reports, these four categories account for over 80% of successful cyberattacks.
-
How long does a typical vulnerability assessment take?
A comprehensive vulnerability assessment typically takes 1-4 weeks depending on the organization’s size and complexity. Automated scanning can be completed within hours, but thorough analysis, prioritization, and reporting require additional time.
-
What compliance requirements mandate vulnerability assessments?
Major compliance frameworks including PCI DSS, HIPAA, SOX, and ISO 27001 require regular vulnerability assessments. Specific requirements vary by regulation, but most mandate quarterly assessments at minimum.
Ready to get started?
You’ll be up and running in no time.
Explore all our features, free for 14 days.