
Cybersecurity moves fast. Either you uncover vulnerabilities before attackers do, or you’re left scrambling to contain the breach. Cybersecurity vulnerability assessment demands a proactive mindset, forcing you to think like an attacker, anticipate threats, and methodically reduce risk. Periodic cybersecurity vulnerability assessments allow you to identify, analyze, and prioritize security gaps across your infrastructure before attackers can exploit them.
White Paper
Closing the Gaps With Automated Vulnerability Management
Why visibility is your first — and most critical — line of defense.
What Is a Cyber Security Vulnerability Assessment?
A cybersecurity vulnerability assessment is a systematic security evaluation that identifies, analyzes, and prioritizes potential security weaknesses across your IT infrastructure. Unlike penetration testing, which actively exploits vulnerabilities, vulnerability assessments focus on discovery and risk mitigation without attempting to breach systems.
Key components of a vulnerability assessment include:
- Asset Discovery: Mapping all systems, applications, and network devices
- Vulnerability Scanning: Using automated tools to detect security weaknesses
- Risk Analysis: Evaluating the potential impact of identified vulnerabilities
- Prioritization: Ranking vulnerabilities based on severity and exploitability
- Remediation Planning: Creating actionable steps to address security gaps
This proactive security process helps organizations identify security gaps before attackers discover them, prioritize remediation efforts based on risk levels, maintain compliance with cybersecurity frameworks like NIST and ISO 27001, and reduce the overall attack surface of their systems.
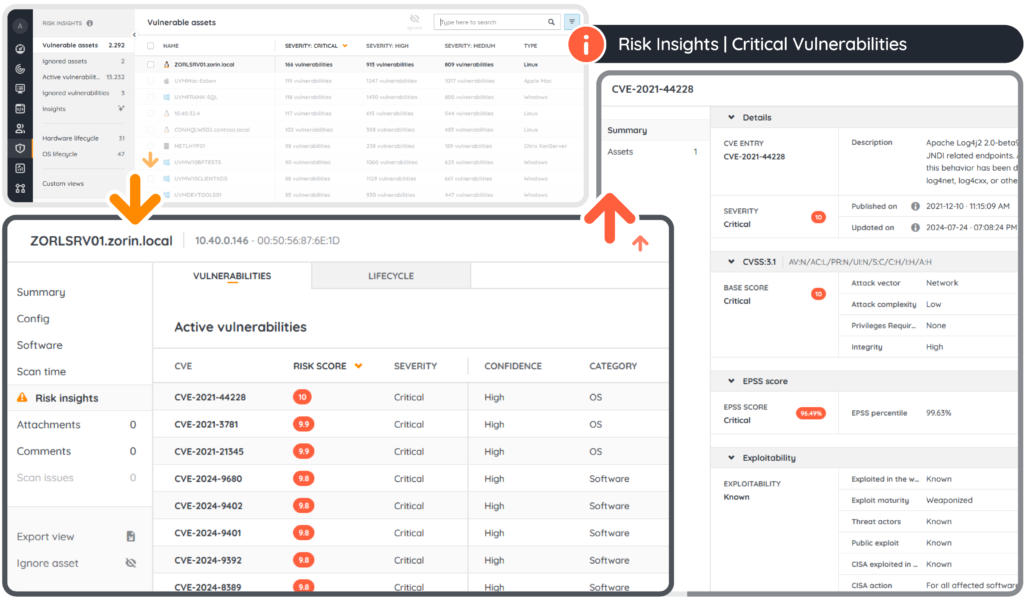
Why Are Vulnerability Assessments Important for Cybersecurity?
Vulnerability assessments are critical because cyber attackers automate their reconnaissance efforts. If your organization isn’t proactively scanning for vulnerabilities, you’re already at a disadvantage. Here’s why they matter:
- Proactive Risk Reduction: Vulnerability assessments help you reduce your attack surface before adversaries can exploit weaknesses, giving you a significant security advantage.
- Compliance Requirements: Many industry regulations and frameworks require regular vulnerability assessments to maintain compliance and avoid costly penalties.
- Operational Continuity: By identifying and fixing vulnerabilities proactively, you prevent potential operational disruptions that could impact business operations and revenue.
What Are the Different Types of Vulnerability Assessments?
Every system presents unique attack vectors, from misconfigured cloud instances to unpatched software and unmanaged devices. Different types of assessments target specific infrastructure components:
Network Vulnerability Assessments
Network vulnerability assessments examine your network perimeter, including firewalls, routers, and switches for misconfigurations and security weaknesses. Automated scanning tools can detect common vulnerabilities, but manual validation remains essential for contextual analysis and accurate risk assessment. Blindly trusting scanner results is a dangerous security misstep.
Regular network assessments help maintain secure and resilient IT infrastructure while ensuring compliance with security standards.
Web Application Vulnerability Assessments
Web applications often expose sensitive data through poorly secured APIs, authentication flaws, and misconfigured cloud storage. These assessments test for common vulnerabilities including:
- SQL injection attacks
- Cross-site scripting (XSS)
- Broken access controls
- Insecure API endpoints
Web application security testing tools like OWASP ZAP, Burp Suite, and manual code reviews should be integrated into your vulnerability analysis process.
Mobile Application Vulnerability Assessments
Mobile applications face unique security challenges due to inconsistent patching and diverse operating environments. Common mobile vulnerabilities include:
- Reverse engineering vulnerabilities
- Insecure data storage
- Weak cryptographic implementations
- Inadequate session management
Mobile security testing frameworks like MobSF and Drozer help uncover these threats before attackers exploit them.
How Do You Conduct a Vulnerability Assessment? A 2-Step Process
Effective vulnerability assessment follows a strategic, two-step process that goes beyond simply running automated scans:
Step 1: Identifying Vulnerabilities and Potential Risks
Start with comprehensive asset discovery. You cannot protect assets you don’t know exist. This process includes:
- Asset Mapping: Document every endpoint, application, and cloud service in your environment
- Shadow IT Discovery: Identify unauthorized applications and services that create blind spots
- Vulnerability Scanning: Use automated tools to detect known security weaknesses
- Manual Validation: Verify scanner results to reduce false positives
Step 2: Prioritizing and Remediating Vulnerabilities
Not all vulnerabilities require immediate action. Effective prioritization considers:
- Exploitability: How easily can attackers exploit the vulnerability?
- Asset Criticality: How important is the affected system to business operations?
- Business Impact: What would happen if this vulnerability were exploited?
For example, a missing patch on a public-facing web server requires immediate attention, while a vulnerability in an internal system with no known exploit may have lower priority.
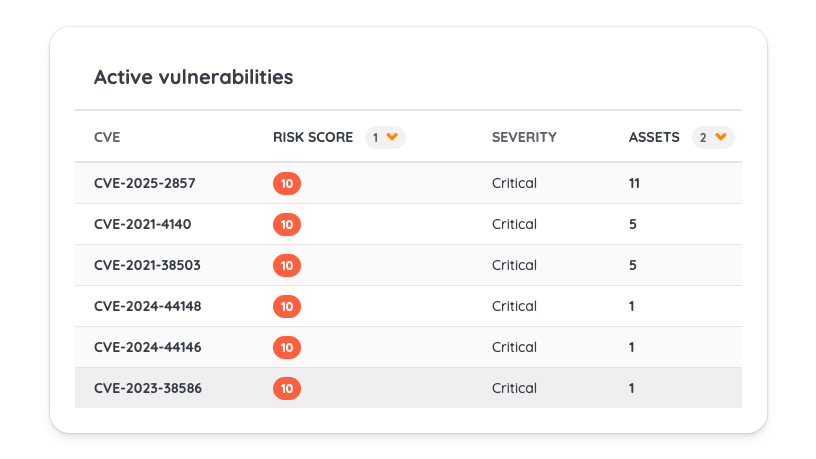
How Can AI Enhance Vulnerability Assessment?
AI-driven solutions enhance traditional vulnerability assessment with:
- Pattern Detection: Analyzing attack data to identify emerging threat patterns
- Predictive Analysis: Forecasting potential security risks based on historical data
- Automated Anomaly Detection: Flagging suspicious activity in real-time
Tools like Darktrace and Microsoft Defender leverage AI to help security teams identify risks faster. However, human expertise remains essential for interpreting findings, filtering false positives, and developing effective response strategies.
What Are the Best Practices for Vulnerability Assessments?
Effective vulnerability assessment goes beyond detection. It minimizes exploitability through strategic implementation:
1. Establish a Vulnerability Management Program
Create a structured program that ensures assessment results feed directly into patching workflows. This approach reduces exposure time and prevents critical fixes from being overlooked.
2. Maintain Regular Patching Schedules
Delayed patching remains one of the biggest security gaps. Critical vulnerabilities should be patched within 24-48 hours, as attackers often analyze security updates to craft exploits targeting unpatched systems.
3. Implement Secure Coding Practices
Security should begin at the development stage. Integrate static and dynamic application security testing (SAST/DAST) into CI/CD pipelines to identify vulnerabilities before deployment.
How Do Vulnerability Assessments Integrate with Overall Security Strategy?
Vulnerability assessments should integrate seamlessly with broader cybersecurity initiatives:
Vulnerability Assessment and Threat Intelligence
Threat intelligence enriches vulnerability data by providing context about active threats. When threat intelligence identifies exploits targeting specific software versions in your environment, vulnerability assessments should reflect elevated risk levels.
Vulnerability Assessment and Incident Response
Vulnerability assessments should inform incident response playbooks. Post-breach forensic analysis should validate whether vulnerability assessment processes effectively identified exploited weaknesses or require improvement.
Continuous Monitoring and Assessment
Implement continuous scanning and monitoring rather than quarterly assessments. Attackers don’t wait for scheduled scans. Tools like CrowdStrike Falcon Spotlight and Tenable.io offer continuous assessment capabilities for real-time threat detection and remediation.
Boost Your Security Strategy with Lansweeper
Without a complete inventory of your IT environment, vulnerabilities slip through the cracks. Lansweeper’s asset discovery and Risk Insights map every device, every piece of software, and every hidden risk, giving you the data you need to act fast. Stop chasing threats in the dark. Get a free demo today and take control of your security strategy.
Lansweeper Demo
See Lansweeper in Action – Watch Our Demo Video
Sit back and dive into the Lansweeper interface & core capabilities to learn how Lansweeper can help your team thrive.
FAQ
-
How often should OT vulnerability assessments be performed?
OT vulnerability assessments should be conducted continuously through automated monitoring, with comprehensive manual assessments performed at least quarterly or whenever significant system changes occur. The frequency may increase based on regulatory requirements and threat landscape changes.
-
What’s the difference between vulnerability assessment and penetration testing?
Vulnerability assessments identify and catalog security weaknesses without exploiting them, while penetration testing actively attempts to exploit vulnerabilities to demonstrate their impact. Vulnerability assessments are broader in scope and performed more frequently, while penetration testing provides deeper analysis of specific vulnerabilities.
-
How much do vulnerability assessments cost?
Vulnerability assessment costs vary widely based on scope, methodology, and organizational size. Automated scanning tools range from free (OpenVAS) to thousands of dollars annually for enterprise solutions. Professional assessment services typically cost $5,000-$50,000 depending on infrastructure complexity and assessment depth.
-
Can small businesses perform their own vulnerability assessments?
Yes, small businesses can perform basic vulnerability assessments using automated tools like OpenVAS, Nessus Essentials, or cloud-based solutions. However, expert validation and manual testing often require cybersecurity expertise that may necessitate external consultation for comprehensive assessments.
-
What compliance frameworks require vulnerability assessments?
Major compliance frameworks requiring regular vulnerability assessments include:
- PCI DSS (Payment Card Industry Data Security Standard)
- HIPAA (Healthcare)
- SOX (Sarbanes-Oxley Act)
- NIST Cybersecurity Framework
- ISO 27001
- CIS Controls
-
How do you prioritize vulnerabilities after assessment?
Prioritize vulnerabilities using the Common Vulnerability Scoring System (CVSS) combined with business context. Consider exploitability, asset criticality, and potential business impact. Address critical vulnerabilities on public-facing systems first, followed by high-risk internal systems based on data sensitivity and operational importance.


