


Keeping an IT environment safe and secure is one of the hardest challenges IT teams face. As networks become larger and more complex, it gets harder to keep track of every single device in your network and which vulnerabilities may be a threat to each of them. And yet it is one of the most important things to be aware of. One update or one patch missed on one device can put your entire network at risk of a cyberattack.

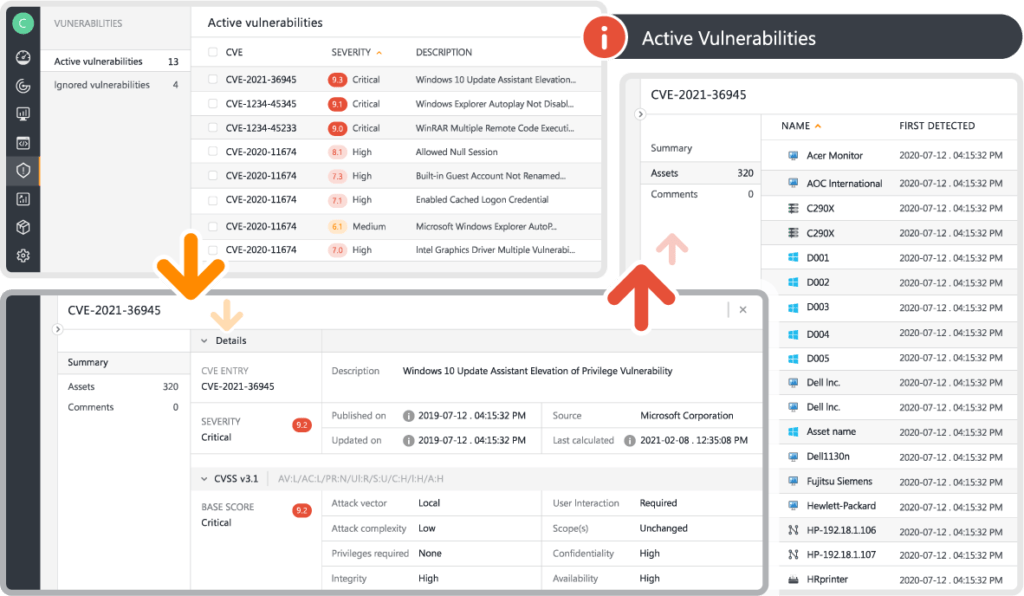
Leverage vulnerability information from the VulnCheck and VulDB databases, to gain visibility of assets that have known vulnerabilities along with a severity indicator, exploitability, and patch information. Easily leverage your data for faster triage and incident response.
Risk Insights provides you with a list of all assets in your technology estate that may be threatened by known vulnerability. Each vulnerability can be ranked by severity based on its CVSS score and includes a list of all at-risk devices, exploitability, and patch information. A short summary of the vulnerability is included, as well as links to official security advisories in case you need more information. The customizable view of the vulnerability list lets you prioritize the information that is most relevant to you. Accurately assess the threat level and prioritize where your intervention is needed the most.
The first step to keeping your network safe is to gain full visibility across your entire IT estate. As Lansweeper continually scans all devices on your network, including their OS and software information, it can easily check all installed versions against any known vulnerabilities. Any devices that are lacking security patches that could leave them exposed will be listed in the Risk Insights. This allows you to quickly take action before the vulnerability can be exploited.
Many industry-leading security frameworks, such as ISO, NIST, and CIS, list vulnerability detection and risk assessment as critical steps in ensuring the safety of your IT environment. Identifying vulnerabilities and at-risk assets in your network plays a crucial role in protecting yourself against cybersecurity attacks.