By combining your asset management and vulnerability management efforts, you can dramatically improve your organization’s security posture.
With so many different pieces of software and infrastructure being used across your organization, we’re guessing that once you implemented a formal system of IT asset management, life became a whole lot easier for your team. You went from spending hours identifying and updating your data (only for it to become out of date again almost instantly) to having a clear, organized, and centralized system with complete control to proactively and effortlessly manage the lifecycle of each of your assets.
But are you using your new IT asset management system to its fullest? Have you realized the vulnerability management benefits yet? If not, read on and we’ll explain how you can make vulnerability management a key part of your asset management strategy and dramatically improve your organization’s security posture.
The Benefits of Effective Asset Management
Like every business, yours has an overstretched IT department, saddled with more responsibility than it can cope with.
With the right asset management software in place, you’ve seen a real difference in what can be achieved, and all your IT assets are now identified, classified, and managed in a manner that optimizes their value to your organization.
You can now:
- Eliminate blind spots across your IT environment by identifying any forgotten or missed assets
- Classify assets based on their value and importance
- Protect assets from loss or damage, and
- Monitor for changes in asset value or importance
This is key for compliance with industry and government legislations and having the data up-to-date and easy to access has eased the stress of preparing for each audit.
The new IT asset management approach should also have significantly enhanced your ability to identify and tackle vulnerabilities. Let us explain.
The Benefits of Effective Asset Management for Vulnerability Management
Vulnerability management is the process of identifying, assessing, and mitigating vulnerabilities in your systems and networks.
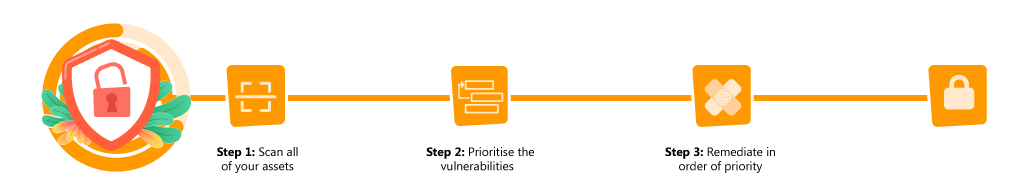
Done properly, you take the following steps:
Step 1: Scan all of your assets to uncover every weakness in your network
Step 2: Prioritise the vulnerabilities in order of criticality to your business ensuring that the biggest, and most likely threats, are tackled first
Step 3: Remediate in order of priority.
This process should work well, provided you have full visibility of all of your assets. This is where IT asset management can really help.
Without full visibility of your IT estate, your sterling vulnerability management efforts will be in vain as just one forgotten device could be running outdated software or even malware that could one day compromise your entire IT infrastructure and drive your business to a devastating halt. You cannot protect what you don’t know about.
Thanks to the insight your solid IT asset management software provides, you can give your vulnerability scanner a full list of assets to monitor, ensuring that nothing is missed. It may even be the case that your IT asset management software has vulnerability scanning capability built-in as is the case with Lansweeper, helping you to move on to Steps 2 and 3 of vulnerability management easily.
On the subject of step 2, the main reason vulnerability prioritization has become so important is the rapid increase in the number of vulnerabilities facing businesses. IT security teams are no longer able to tackle every issue and there are three ways businesses currently prioritize their risk: manual triage; using a third-party vulnerability management tool; or using a personalized automated prioritization platform.
The third option will of course give you the best and most personalized results for your business. You set rules on how vulnerabilities should be prioritized and assigned to remediation teams and it will sort the data from every new scan within minutes, ensuring the vital work of remediating critical vulnerabilities happens without delay.
When determining what is critical, IT asset management is of great value again. This is because it gives you a crystal clear understanding of your IT environment in terms of the value of assets, helping you to correctly prioritize the vulnerabilities affecting the most crucial systems over those that are less frequently used.
These are two huge benefits that asset management brings to vulnerability management: full visibility of your IT estate to identify every weakness lurking within it; and a rich, contextual understanding of how each asset operates and brings value to your organization so that you can prioritize the vulnerabilities facing you.
How Vulnerability Management Can Help Improve Your Asset Management
Conversely, a solid vulnerability management program can also enhance your asset management strategy because it teaches you the value of having a full and up-to-date inventory of everything within your IT estate. In combination with a good vulnerability management tool, you can use the data collected by your ITAM tool to inform your future asset management decisions.
How Lansweeper’s IT Asset Data Can Improve Your Vulnerability Management
Working in IT security is tough and overwhelming but having the right tools in place to help you can make a sizeable difference not just to your productivity but to your peace of mind as well.
IT asset management software and vulnerability management technology make a powerful combination and will help you more effectively identify and mitigate risks to your organization. Asset Management data is a fundamental starting point for implementing any security measures across your organization. You can’t protect what you don’t know you have.
Lansweeper gives you a complete and comprehensive overview of all your IT assets, their software installations, and other asset-specific information. All this is valuable data to assess security threats, and vulnerabilities, and respond to security incidents.
In order to respond quickly to potential threats, Lansweeper’s Security Insights leverage the collected asset data immediately in the Lansweeper console. Drawing information from the NIST Vulnerability Database, it gives you a complete overview of all known vulnerabilities that are a threat to your assets. This way you can easily track which assets may be at risk, as well as the severity of each vulnerability, allowing you to prioritize and immediately intervene where it is needed the most.
Ready to get started with your vulnerability management? Try Lansweeper now or get in touch with our sales team.

