A Guide to Risk-Based Vulnerability Management with Lansweeper
Contents

Over the past few years, organizations have faced an ever-growing range of cyber threats. Effective policies for risk analysis and vulnerability management have become an essential part of any security strategy. By systematically identifying weaknesses within an organization’s systems and infrastructure, vulnerability management can mitigate the likelihood and impact of security breaches. A risk-based approach allows you to prioritize the vulnerabilities that pose the greatest threat to your business operations, ensuring resources are focused where they matter most.
Lansweeper’s powerful discovery capabilities and Risk Insights provide a strong foundation for risk analysis and vulnerability management. They also strengthen information system security by uncovering misconfigurations and hidden risks before attackers can exploit them.
Closing the Gaps With Automated Vulnerability Management
Why visibility is your first — and most critical — line of defense.
Download the White PaperWhat Is Risk-Based Vulnerability Management?
Simply put, risk-based vulnerability management is the practice of spotting weaknesses in your IT
systems, and then prioritizing and mitigating them based on the actual risk they pose to your business operations. Unlike traditional vulnerability management, which only considers severity ratings like CVSS scores, a risk-based approach factors in business context, asset criticality, and potential
impact.
For example, a “critical” vulnerability on a test server may matter less than a “medium” vulnerability on a production server that stores sensitive customer data.
Many securty frameworks, like the NIS 2 Directive (Article 21) for example, call for effective policies for risk analysis and information system security. Adopting a risk-based approach to vulnerability management is one of the most practical ways you’ll meet these requirements while strengthening your defenses.
Why Vulnerability Management?
Vulnerability management is a vital part of any cybersecurity strategy. It consists of systematically identifying, assessing, prioritizing, and mitigating vulnerabilities in software, systems, and networks. This enhances your security posture in several ways:
- Reduce risk exposure: By patching or mitigating flaws before attackers can exploit them.
- Protect operations: Preventing costly downtime from ransomware, data theft, or system disruptions.
- Support compliance: Many frameworks, including NIS 2, ISO 27001, and SOC2, require vulnerability management.
- Improve efficiency: Resources are directed toward the vulnerabilities that actually matter.
Proper risk and vulnerability management helps organizations avoid potential threats by proactively identifying weaknesses before attackers can take advantage. Regularly assessing your IT infrastructure for vulnerabilities enables businesses to detect vulnerabilities promptly, reducing the window of opportunity for cyber attackers. Based on the severity of each vulnerability, you can prioritize your remediation efforts and allocate resources accordingly.
How Does Risk-Based Vulnerability Management Work?
When taking a risk-based approach to threat and vulnerability management, instead of treating all vulnerabilities equally, you prioritize your respons based on these 3 criteria:
- Severity (CVSS scores, exploitability, availability of fixes).
- Business impact (Does the asset store sensitive data? Is it mission-critical?).
- Likelihood of exploitation (Are attackers actively exploiting it in the wild?).
Risk-based vulnerability assessment does not rely only on industry standards (like a CVSS score) to determine which vulnerabilities are the biggest threat. Instead, it also takes into account how the vulnerability affects your organization. That way, security teams can prioritize remediation efforts where they matter most.
What Is the Difference Between Risk and Vulnerability?
It is important to keep in mind the difference between risk and vulnerability.
- Vulnerability: A flaw or weakness in a system, network, application, or process.
- Risk: The likelihood that the vulnerability will be exploited and the potential impact if it is.
For example:
- A SQL injection flaw on an isolated test database = vulnerability with low risk.
- A weak admin password on your ERP system = vulnerability with high risk.
Understanding this distinction is the foundation of risk-based vulnerability management.
Step-by-Step Vulnerability Management with Lansweeper
Lansweeper’s unrivaled asset discovery capabilities can give you an edge in every step of the vulnerability management process.
- Asset Inventory: How do you build a complete asset inventory?
As we all know by now, you can’t protect what you don’t know you have. Every vulnerability management strategy should start with a comprehensive inventory of all assets within the organization’s infrastructure. Lansweeper automatically discovers hardware, software, network devices, user accounts, and data repositories, both on-prem and in the Cloud. - Vulnerability Identification: How do you identify vulnerabilities?
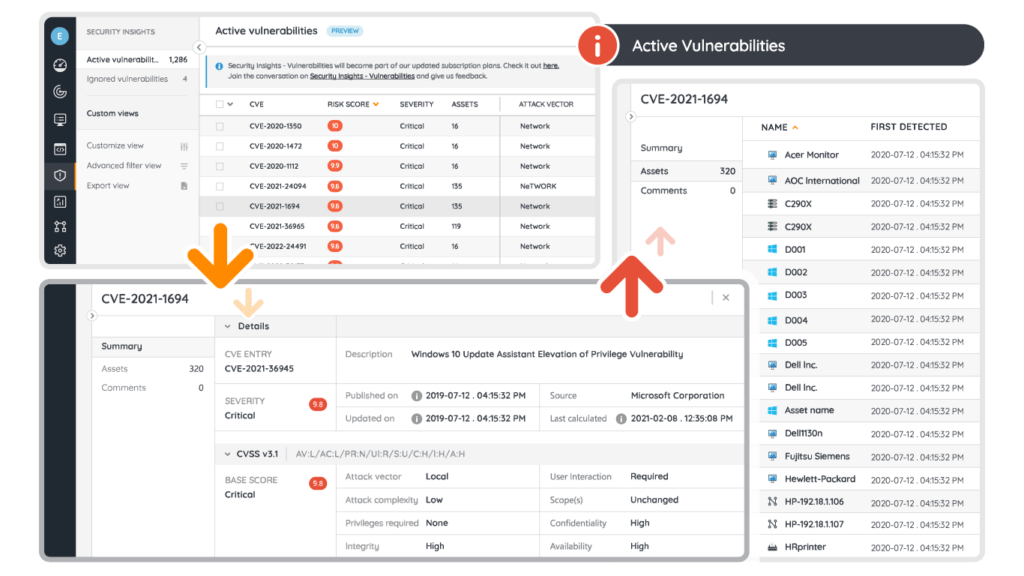
Identify potential weaknesses in the organization’s systems and software. Lansweeper’s Risk Insights draws information from the VulnCheck, CISA, and MSRC databases to map known vulnerabilities to affected assets. - Vulnerability Classification: How do you classify vulnerabilities?
Classify known vulnerabilities based on severity, exploitability, and potential impact on your organization’s assets and operations. The information in Risk Insights will tell you the CVSS score of a vulnerability and which assets are at-risk. This lets you distinguish between “high-severity but irrelevant” issues and “medium-severity but critical” ones. - Risk Assessment: How do you assess risk?
You want to know what the potential impact of identified vulnerabilities is on your organization’s critical assets and operations. Consider factors such as the likelihood of exploitation, the value of the asset, and potential consequences. Use Lansweeper’s Diagrams to visualize your network and see what other assets and systems may be impacted by a breach. - Prioritization: How do you prioritize vulnerabilities?
Prioritize vulnerabilities based on the level of risk they pose to your organization. High-risk vulnerabilities that are easy to exploit and have severe consequences should be your priority, followed by medium and low-risk vulnerabilities. - Remediation and Mitigation: How do you remediate and mitigate?
Develop and implement remediation and mitigation strategies to address identified vulnerabilities. This may involve patching software, updating configruations, strengthening authentication, network segmentation, decommissioning obsolete assets, and more.
Why Do Network Misconfigurations Matter?
Some of the most common — and most avoidable — security issues stem from simple misconfigurations. Think of them like leaving doors inside your building unlocked. Once attackers make it into the building, these gaps make it easier for them to move around laterally and cause more damage. And yet, these issues are often overlooked.
Common misconfigurations Lansweeper detects include:
- Missing antivirus or encryption
- Unauthorized local admins
- Outdated drivers and certificates
- Unpatched browsers and OS
- Weak firewall or BitLocker settings
By closing these gaps, you reduce the attack surface and minimize the potential impact of a breach.
Start Managing Your Vulnerabilities Now
Risk analysis is an excellent place to start, whether you’re aiming for compliance with security frameworks or simply strengthening your overall cybersecurity posture. Vulnerability management plays a critical role in this process, offering a structured way to identify and address weaknesses in your IT environment, reduce your attack surface, and minimize the risk of security breaches.
By adopting a proactive, risk-based approach, organizations can stay ahead of evolving threats and ensure their defenses remain resilient. Ultimately, effective vulnerability management is not just about fixing problems as they arise, but about building a sustainable strategy that supports long-term security and business continuity.
See Lansweeper in Action – Watch Our Demo Video
Sit back and dive into the Lansweeper interface & core capabilities to learn how Lansweeper can help your team thrive.
WATCH DEMOFrequently Asked Questions
-
What is the difference between vulnerability management and patch management?
Patch management is about keeping your software up to date by applying the latest updates and security patches. Vulnerability management goes further — it’s a
continuous process of finding weaknesses, understanding how risky they are, prioritizing fixes, and taking action. Sometimes the solution is a patch, but other times it could mean changing configurations, tightening access controls, or even retiring outdated systems. -
How often should vulnerability scans be performed?
Best practice suggests scanning at least once a month, but the right frequency depends on your industry and risk profile. Organizations that handle sensitive financial or healthcare data often scan weekly or even daily. The key is consistency. Scanning regularly reduces the window of opportunity for attackers to exploit unpatched vulnerabilities.
-
Is Lansweeper a vulnerability scanner?
Not exactly. Lansweeper isn’t a traditional vulnerability scanner. Instead, it’s an asset discovery and risk insights platform that gives you the full picture of your IT environment. It integrates vulnerability data (from sources like VulnCheck and MSRC) with your asset inventory, showing which systems are at risk and helping you prioritize fixes. Many organizations use Lansweeper alongside their existing scanners to add essential context.
-
What’s the benefit of a risk-based approach compared to traditional vulnerability management?
Traditional vulnerability management often relies heavily on severity scores (like CVSS) without considering your unique business context. A risk-based approach looks at the actual impact on your systems and operations. This means you’re not wasting resources chasing low-impact issues while critical risks remain unaddressed.
-
Can risk-based vulnerability management help with compliance requirements?
Yes. Frameworks such as NIS 2, ISO 27001, HIPAA, and SOC 2 all require organizations to manage vulnerabilities effectively. A risk-based approach helps
demonstrate that you’re not only finding weaknesses but also prioritizing remediation in a structured, business-aware way. This makes audits easier and strengthens your overall compliance posture.
Ready to get started?
You’ll be up and running in no time.
Explore all our features, free for 14 days.