⚡ TL;DR | Go Straight to the FortiClient Version Audit Report
Fortinet has released security patches in response to a critical vulnerability in FortiClientLinux. When successfully exploited the issue could lead to arbitrary code execution which can in turn compromise the integrity of sensitive data and systems. You can check the version of any instances of FortiClient installations in your network using the version audit report, to make sure they are all on the fixed version.
FortiClient Linux Vulnerability CVE-2023-45590
The vulnerability tracked as CVE-2023-45590 is described in Fortinet’s advisory as “An Improper Control of Generation of Code (‘Code Injection’) vulnerability” in FortiClientLinux. It received a critical CVSS score of 9.4 and could allow an unauthenticated attacker to execute arbitrary code by tricking a FortiClientLinux user into visiting a malicious website. Arbitrary code execution can compromise the integrity of sensitive data and systems.
Fortinet also received patches for 2 more high-severity issues:
- CVE-2023-45588 and CVE-2024-31492: An external control of file name or path vulnerability in FortiClientMac’s installer. This could allow a local attacker to execute arbitrary code or commands.
- CVE-2023-41677: An insufficiently protected credentials vulnerability in FortiOS and FortiProxy. This issue could allow an attacker to obtain the administrator cookie in rare and specific conditions.
Update Vulnerable Fortinet Installations
Each of these vulnerabilities affects a different range of Fortinet products. Users are advised to update vulnerable instances of FortiClientLinux, FortiClientMac, FortiOS, and FortiProxy to the latest version as found in the table below. Make sure to update any affected devices as soon as possible.
CVE-2023-45590: FortiClientLinux
| Product and Version | Affected Version | Solution |
| FortiClientLinux 7.2 | 7.2.0 | Upgrade to 7.2.1 or above |
| FortiClientLinux 7.0 | 7.0.6 through 7.0.10 | Upgrade to 7.0.11 or above |
| FortiClientLinux 7.0 | 7.0.3 through 7.0.4 | Upgrade to 7.0.11 or above |
CVE-2023-45588 and CVE-2024-31492: FortiClientMac
| Product and Version | Affected Version | Solution |
| FortiClientMac 7.2 | 7.2.0 through 7.2.3 | Upgrade to 7.2.4 or above |
| FortiClientMac 7.0 | 7.0.6 through 7.0.10 | Upgrade to 7.0.11 or above |
CVE-2023-41677: FortiOS and FortiProxy
| Product and Version | Affected Version | Solution |
| FortiOS 7.4 | 7.4.0 through 7.4.1 | Upgrade to 7.4.2 or above |
| FortiOS 7.2 | 7.2.0 through 7.2.6 | Upgrade to 7.2.7 or above |
| FortiOS 7.0 | 7.0.0 through 7.0.12 | Upgrade to 7.0.13 or above |
| FortiOS 6.4 | 6.4.0 through 6.4.14 | Upgrade to 6.4.15 or above |
| FortiOS 6.2 | 6.2.0 through 6.2.15 | Upgrade to 6.2.16 or above |
| FortiOS 6.0 | 6.0 all versions | Migrate to a fixed release |
| FortiProxy 7.4 | 7.4.0 through 7.4.1 | Upgrade to 7.4.2 or above |
| FortiProxy 7.2 | 7.2.0 through 7.2.7 | Upgrade to 7.2.8 or above |
| FortiProxy 7.0 | 7.0.0 through 7.0.13 | Upgrade to 7.0.14 or above |
| FortiProxy 2.0 | 2.0 all versions | Migrate to a fixed release |
| FortiProxy 1.2 | 1.2 all versions | Migrate to a fixed release |
| FortiProxy 1.1 | 1.1 all versions | Migrate to a fixed release |
| FortiProxy 1.0 | 1.0 all versions | Migrate to a fixed release |
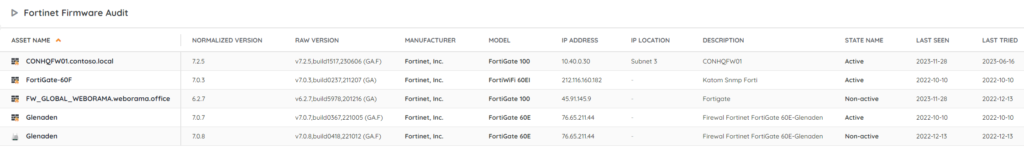
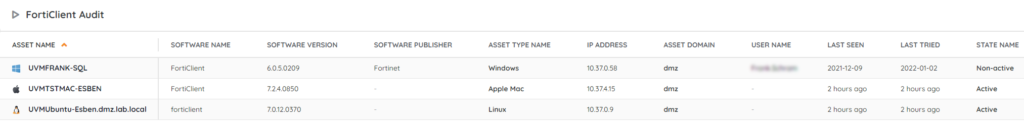
Discover Vulnerable Fortinet Installs
Our team has added 2 new reports to Lansweeper to help you locate vulnerable Fortinet products, 1 for FortiClient and 1 for Fortinet Firmware. This will give you a list of instances of Fortinet products and their versions, so you can more easily check if they are all up to date. You can get the reports via the links below.