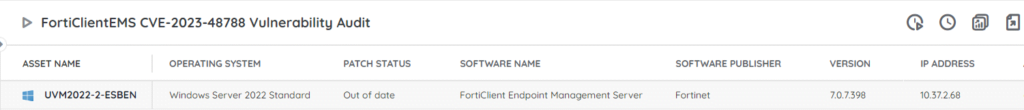
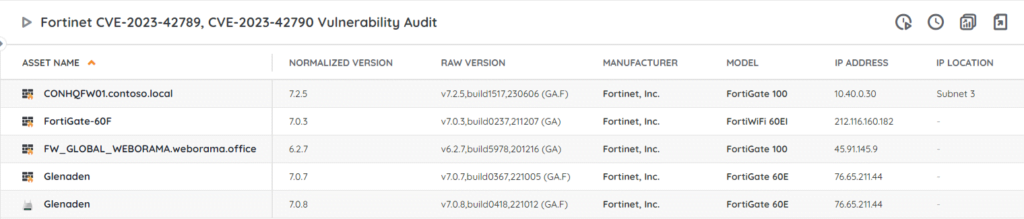
⚡ TL;DR | Go Straight to the FortiClientEMS Vulnerability Audit Report or the FortiOS/FortiProxy Vulnerability Audit Report.
Fortinet has fixed a couple of critical code execution vulnerabilities in FortiOS, FortiProxy, and FortiClientEMS. When successfully exploited these vulnerabilities could lead to code execution which can in turn compromise the integrity of sensitive data and systems. We have added a new report to Lansweeper to help you locate vulnerable devices.
Fortinet Vulnerabilities CVE-2023-48788, CVE-2023-42789, and CVE-2023-42790
Fortinet’s advisory describes the vulnerability tracked as CVE-2023-48788 as “an improper neutralization of special elements used in an SQL Command” in FortiClientEMS. It received a critical CVSS score of 9.3. So far there are no reports of the issue being exploited in the wild. If successfully exploited it could allow an attacker to execute unauthorized code or commands via specially crafted requests. This canin turn compromise the integrity of sensitive data and systems.
CVE-2023-42789 and CVE-2023-42790 are respectively an out-of-bounds write and a Stack-based buffer overflow vulnerability in FortiOS & FortiProxy. Both received a critical CVSS score of 9.3. An attacker with access to captive portal could use these bugs to execute arbitraty code via specifically crafted HTTP requests.
Update Vulnerable Fortinet Installations
While there are no reports yet of any of these vulnerabilities being exploited in the wild, it is still important to update vulnerable devices as soon as possible. Fortinet vulnerabilities are often a target in ransomware or cyberespionage campaigns.
To patch this vulnerability Fortinet’s advisories recommend updating affected of FortiOS, FortiProxy, and FortiClientEMS instances to the latest version as found in the table below. Make sure to update any affected devices as soon as possible.
If it is not possible for you to update right away, you can disable SSL VPN as a workaround.
| Product and Version | Affected Version | Solution |
| FortiClientEMS 7.2 | 7.2.0 through 7.2.2 | Upgrade to 7.2.3 or above |
| FortiClientEMS 7.0 | 7.0.1 through 7.0.10 | Upgrade to 7.0.11 or above |
| FortiOS 7.4 | 7.4.0 through 7.4.1 | Upgrade to 7.4.2 or above |
| FortiOS 7.2 | 7.2.0 through 7.2.5 | Upgrade to 7.2.6 or above |
| FortiOS 7.0 | 7.0.0 through 7.0.12 | Upgrade to 7.0.13 or above |
| FortiOS 6.4 | 6.4.0 through 6.4.14 | Upgrade to 6.4.15 or above |
| FortiOS 6.2 | 6.2.0 through 6.2.15 | Upgrade to 6.2.16 or above |
| FortiProxy 7.4 | 7.4.0 | Upgrade to 7.4.1 or above |
| FortiProxy 7.2 | 7.2.0 through 7.2.6 | Upgrade to 7.2.7 or above |
| FortiProxy 7.0 | 7.0.0 through 7.0.12 | Upgrade to 7.0.13 or above |
| FortiProxy 2.0 | 2.0.0 through 2.0.13 | Upgrade to 2.0.14 or above |
For the vulnerabilities affecting FortiOS and FortiProxy, Fortinet also offers a workaround if it is not possible for you to update right away.
Discover Vulnerable Fortinet Installs
Our team has added 2 new reports to Lansweeper to help you locate vulnerable Fortinet devices, 1 for FortiClientEMS and 1 for FortiOS and FortiProxy. This will give you an actionable list of devices that are running an affected version and need you to take action. You can get the report via the links below.