⚡ TL;DR | Go Straight to the ConnectWise ScreenConnect Vulnerability Audit Report
Earlier this week ConnectWise disclosed 2 vulnerabilities in their ScreenConnect remote desktop and access software. Technical details and proof-of-concept exploits are now available for both vulnerabilities. When successfully exploited the vulnerabilities can lead to remote code execution. ConnectWise is once again urging all users to update all on-premise servers to version 23.9.8.
ScreenConnect Vulnerabilities CVE-2024-1708 and CVE-2024-1709
The vulnerabilities have been assigned the identifiers CVE-2024-1708 and CVE-2024-1709 by CISA. They are an improper limitation of a pathname to a restricted directory (“path traversal”) (CVSS score 8.4) and an authentication bypass using an alternate path or channel vulnerability (CVSS score: 10) respectively. If exploited, the vulnerabilities could lead to remote code execution which could in turn compromise confidential data and critical systems. You can read more in ConnectWise’s advisory.
Update Vulnerable ScreenConnect Installs
In an update to their advisory ConnectWise confirmed that multiple ScreenConnect accounts have been compromised by threat actors. The vulnerabilities affect any ScreenConnect servers version 23.9.7 and earlier. They are urging users to update any on-promise servers to version 23.9.8 as soon as possible.
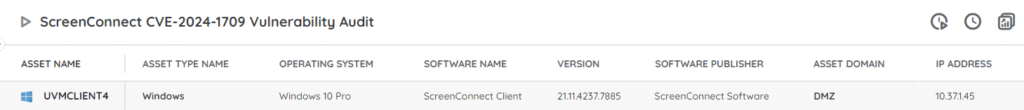
Discover Vulnerable ScreenConnect Installs
Our team has added a new report to Lansweeper to help you locate vulnerable ScreenConnect servers. This way you have an actionable list of servers that still need to be updated to the newest version. You can get the report via the link below.