Cyberattacks have been on the rise worldwide for years now, and they show no signs of stopping. Data from 2022 showed an increase of 38% compared to the previous year. In the healthcare industry, that increase was 86%. The wealth of private data that healthcare providers have stored, as well as their concern for patient safety makes them coveted targets for cybercriminals.
What Makes the Healthcare Industry a Prime Target?
Cyberattacks range from malware to ransomware, to denial of service (DDoS) attacks. One thing they all have in common is that they threaten the security and integrity of systems and confidential data as well as disrupt patient care and treatments. 2 things make healthcare providers a coveted target for cybercriminals: patient data, and the leverage of patient safety.
1. Valuable Patient Data up for Grabs
One major concern in the healthcare industry is patient privacy. Healthcare organizations collect a lot of personal and sensitive data from their customer. Recovering from the theft of this information takes a lot of time and money and that would be the least of anyone’s worries. Losing this data to cybercriminals will not only damage the trust between healthcare providers and their patients. On top of that, you could be faced with severe penalties from privacy legislation like HIPAA, which requires healthcare systems to protect patient data.
In extension to patients’ private information being up for grabs, any loss of medical records could jeopardize the care delivered to your patients. Lost or altered information could delay effective care being delivered or even endanger the patient further.
2. A Direct Threat to Patient Safety
While cyberattacks are a problem in all industries, they are uniquely dangerous in the healthcare industry. To healthcare providers cyberattacks don’t just breach privacy and cause financial loss. Loss of data and disruption of processes can also possibly endanger the health, safety, and even the lives of patients.
Ransomware attacks can interfere with patients’ sensitive medical information, but also interrupt medical systems and procedures, thereby putting your patients’ safety and well-being at risk. Hospitals that were victims of security breaches or ransomware saw delays in life-saving treatments, ambulances being diverted en route, and critical equipment failing. Disruptions in operations and patient care can last weeks or even months.
When a network is under attack, organizations will often shut down their systems to avoid the attack spreading further into the network. Unfortunately, this leads to extra costs and downtime. Healthcare providers in particular often can’t afford to shut down critical systems without jeopardizing patient care. While ransomware attacks don’t always lead to patient deaths, a report by CISA revealed that ransomware attacks do lead to higher mortality rates. They can prevent medical staff from effectively administering critical care or delay lifesaving procedures.
3. Most Likely to Pay Ransom
Attackers are aware of these things and it puts them in a position of power against their intended target. Once security has been breached, very few healthcare providers are willing to risk their patients’ safety by resisting the attacker’s terms. In 2021, 61% of healthcare organizations that were the target of a ransomware attack paid the ransom in order to regain their systems. This is the highest percentage in any sector.
All of this has led to an increase in attacks on healthcare facilities. In 2020 34% of healthcare organizations in the US reported being the target of a ransomware attack. In 2021, this number was up to two-thirds of healthcare organizations. In 2022 there was another increase in attacks by 86%
How Do You Deal With a Ransomware Attack?
The most common way that ransomware finds its way onto a system is via phishing. A malicious email masquerades as a company or personal email to lure its target into opening the email and clicking an infected link or opening a malicious file. From there the attacker can gain access to the victim’s computer or other parts of the network. One inattentive employee clicking a link can put the entire organization at risk.
Once the ransomware is in place, users are denied access to files, systems, or even entire networks, until the ransom is paid. Sometimes attackers will also threaten to leak sensitive data as an additional incentive. Cybersecurity experts and law enforcement advice against paying the ransom, because there’s no guarantee that the attacker will decrypt the files again. Successful attacks also encourage more ransomware attacks in the future.
In large networks, attackers also make use of vulnerabilities. These are often found in older servers and operating systems. Older IT is sometimes kept around due to budget constraints or to run older software or equipment that was designed to work with the older systems. Unfortunately, legacy equipment is often more vulnerable to attacks.
What Can You Do to Protect Your Network?
Cyberattacks in the healthcare industry are not just an IT issue. Not only do they compromise the organization’s internal data, but it also puts patient safety at risk. It is not only a technical issue. It is a security risk for the entire enterprise as well as its patients. It should be considered a strategic priority issue.
By considering cyber threats in the context of your patient’s safety and privacy, you can not only protect your IT estate but also guarantee that you can continue to deliver effective, high-quality care, without disruptions that could negatively impact clinical outcomes.
Though ransomware attacks have become more common and aggressive, many are preventable according to a 2019 Gartner report. To effectively protect your organization from attacks what you need are preventative measures, a plan of action for when an attack occurs, and a strategy that goes beyond the IT department. Cybersecurity can only be effective with the cooperation of your entire staff. You can take the following steps to strengthen your cybersecurity profile.
- Strengthen your network defenses. Arm yourself with strong firewalls and antivirus software and encrypt sensitive data. Replace any outdated systems and software to minimize vulnerabilities. Back up your systems to restore compromised data and systems in the event of an attack.
- Educate your employees. As mentioned before, many attacks try to exploit human error. A single mistake can compromise your entire network. Teach your employees to recognize the signs of an attack and how to take preventative measures in their day-to-day tasks. Stress the importance of cybersecurity as a matter of patient safety.
- Treat cybersecurity as a strategic and enterprise-level matter. It is not only the IT team’s issue, the entire organization could be at risk when the bad guys set their eyes on you. Regularly audit and update your organization’s cyber risk profile and strategy. The threat landscape is always evolving and so should your strategy to deal with threats.
- Make the matter of cybersecurity someone’s number one priority, and give them the tools and authority to effectively protect you from cyber-attacks.
- Set up Multifactor authentication (MFA). MFA requires users to provide 2 or more credentials to authenticate a login. This can prevent attackers from using a single user credential to penetrate further into your network.
- Segment your network. By dividing your network into sections, you can stop an attack from spreading to your entire organization. You can quarantine the affected segment without the need to shut down your entire network. This way most of your organization will remain unaffected by the attack and can continue to operate.
Why Lansweeper’s Ready-To-Use IT Inventory Is a Lifesaver in a Ransomware Attack
You can’t protect what you don’t know you have, so IT Asset Management (ITAM) is a critical first step in your cybersecurity strategy. Lansweeper continually and automatically scans your network, detecting any connected device, and providing your IT security team with complete and detailed information about your IT estate. The granular view of all of your connected hardware and software helps you proactively mitigate the risk of attacks. Should an attack occur you can use the same accurate data to stop it in its tracks.

Stay On Top of Patches and Updates
As your technology infrastructure grows in size and complexity, keeping up with updates and patches becomes increasingly challenging. Manually tracking these changes is no longer an option.
Lansweeper automatically discovers and identifies all connected assets, and creates a complete and always-accurate inventory, saving time and eliminating human error. Your IT asset inventory is now always current and complete. You can easily see which assets are still missing updates or patches to make sure that IT estate is always properly secured.
Protect Unknown and Rogue Devices
In the interest of productivity and mobility bring-your-own-device (BYOD), policies are increasingly popular. This results in unknown numbers of potentially unprotected devices entering your network and opening it up to additional risk.
Using device recognition technologies, Lansweeper detects unknown and rogue devices, then reports back detailed information about the device, just like any other asset. Once they are discovered, you can determine their origin and decide whether to add them to Lansweeper to perform a deep scan to collect more data.
Isolate and Mitigate Security Incidents
The playing field of hackers is constantly changing. New methods and techniques allow them to circumvent any precautions you may take. If an attack does occur, Lansweeper helps you to identify and isolate impacted machines, and to shut them down to stop the spread.
Be Prepared
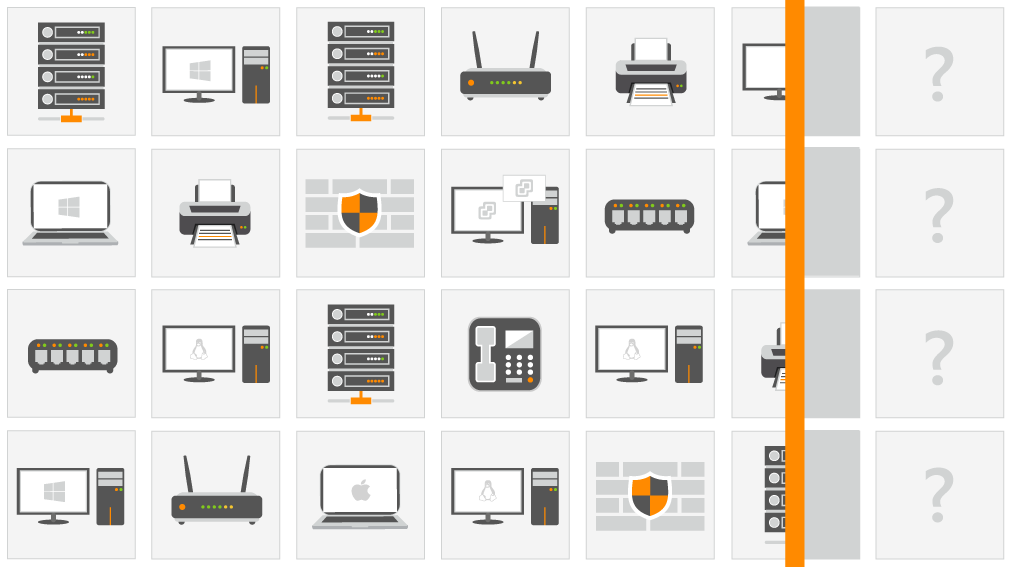
Lansweeper detects and recognizes every asset that touches your network, eliminating blind spots and giving you full visibility across the IT infrastructure. It can see assets that aren’t properly encrypted, unauthorized software installations, and vulnerabilities that require immediate patching. Automated alerts will let your team know when they need to jump into action, closing the window on malicious attacks.
Lansweeper’s detailed information shows you which devices are most vulnerable or contain the most sensitive information so you can prioritize your work and devise a plan of counter-attack. Even though you may not be able to prevent an attack, you can prepare to repel as many as possible. Take proactive measures now by ensuring you have the insights you need to spot, isolate and stop an attack.