
Discover assets you don’t even know about and eliminate blind spots.
Anticipate potential cybersecurity attacks with audit preventive measures.
Get an instant cybersecurity audit across your entire network through valuable reports.
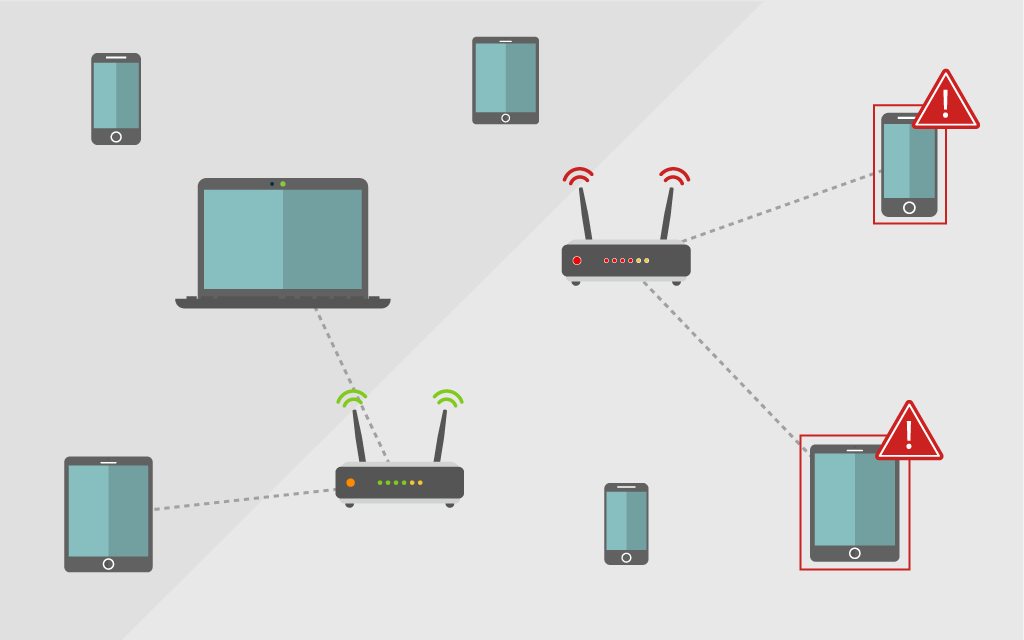
Shadow IT, Bring-Your-Own-Device (BYOD), and IoT are inevitable components of modern enterprise networks. With more and more assets connecting to the corporate network, rogue cyber risks are growing fast, and many of these assets may be unknown and unmanaged by IT.
As these undetected assets pose serious security and compliance risks, the ability to detect unknown, unauthorized and potential rogue devices is an essential first step in IT security. This will prevent unauthorized network access. We all know every good security program starts with an understanding of all the assets connected to the network.
Ensuring that unknown devices -which are far more likely to become a rogue network device- are detected the moment they enter your organization’s network is crucial.
Lansweeper’s Asset Radar continuously scans and sniffs network packets to detect unknown and potential rogue hosts. It operates in real-time, scanning unobtrusively for connected devices. No matter where and when devices join the network, Asset Radar eliminates the possibility of unnoticed transient devices that quickly connect and disconnect in between regularly planned scans. By setting up email alerts, administrators can be instantly notified about the detection of any unauthorized assets.
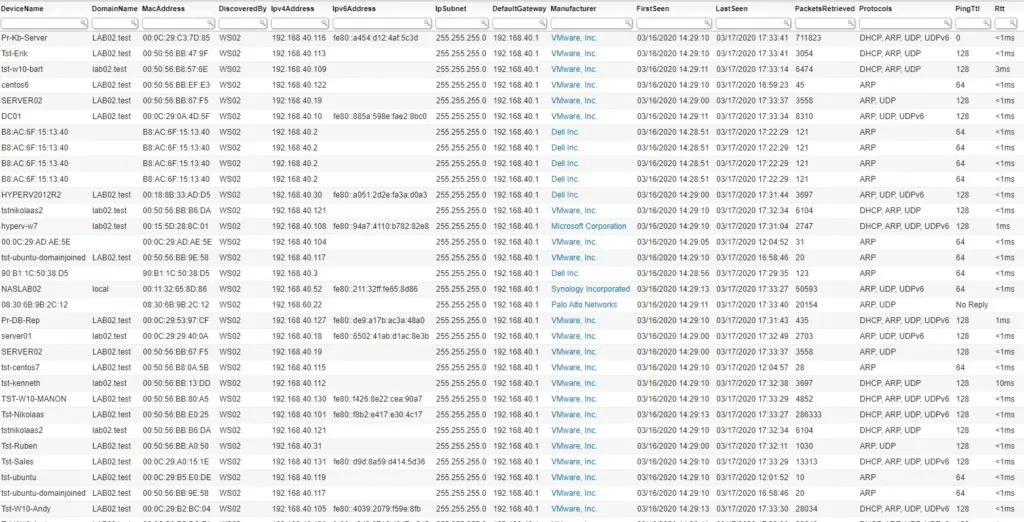
Rogue device detection management requires recognizing known devices so that you can mitigate threats posed by unknown assets. All packets discovered via Asset Radar are captured in detailed information logs.
These logs show the type of packet that was captured, as well as the retrieved information from these packets: device name, MAC, IPv4 and IPv6 addresses, and specific network information such as the default gateway, subnet, PingTTL, and RTT. All log entries can be individually evaluated and delivered to the active scanning queue for more in-depth analysis. This also helps you prevent rogue access points.
Ensuring these devices are detected when they enter your organization’s network is crucial, as these new and unknown devices could easily become a security risk. But this is only a first step. Our advanced Credential-free Device Recognition technology recognizes and identifies every device on the network — even previously non-scannable devices — without the need for credentials or complex pre-configurations, giving you unprecedented insight and control across your entire IT estate.
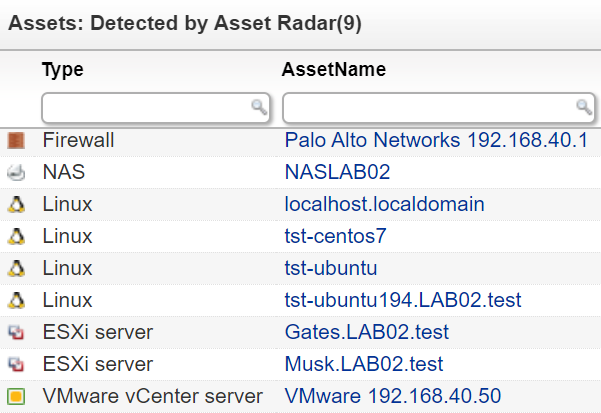
With Lansweeper’s advanced technology, you can instantly detect and recognize unknown assets that may only be briefly connected to the network with our rogue device detection tool. Fast-moving transient devices will be picked up and leave a trail in the log files. Once rogue or unknown devices are detected & recognized, our active scanning methods can be selectively applied to provide more in-depth asset information.
By combining passive and active scanning, you’ll achieve complete visibility of your entire IT environment and eliminate all blind spots. Detecting rogue devices instantly will enable you to take security measures to block unauthorized access.
The attack surface encompasses all points of entry that can serve as attack vectors for unauthorized users to gain access to a system for malicious reasons. Cyber Asset Attack Surface Management (CAASM) helps to identify all potentially vulnerable assets before an attacker gets in. Detecting and preventing attacks won’t be possible without complete and accurate technology asset data. Learn how Lansweeper enables CAASM by providing visibility and actionable insights across your Technology Estate in this whitepaper.
Explore all our features, free for 14 days.