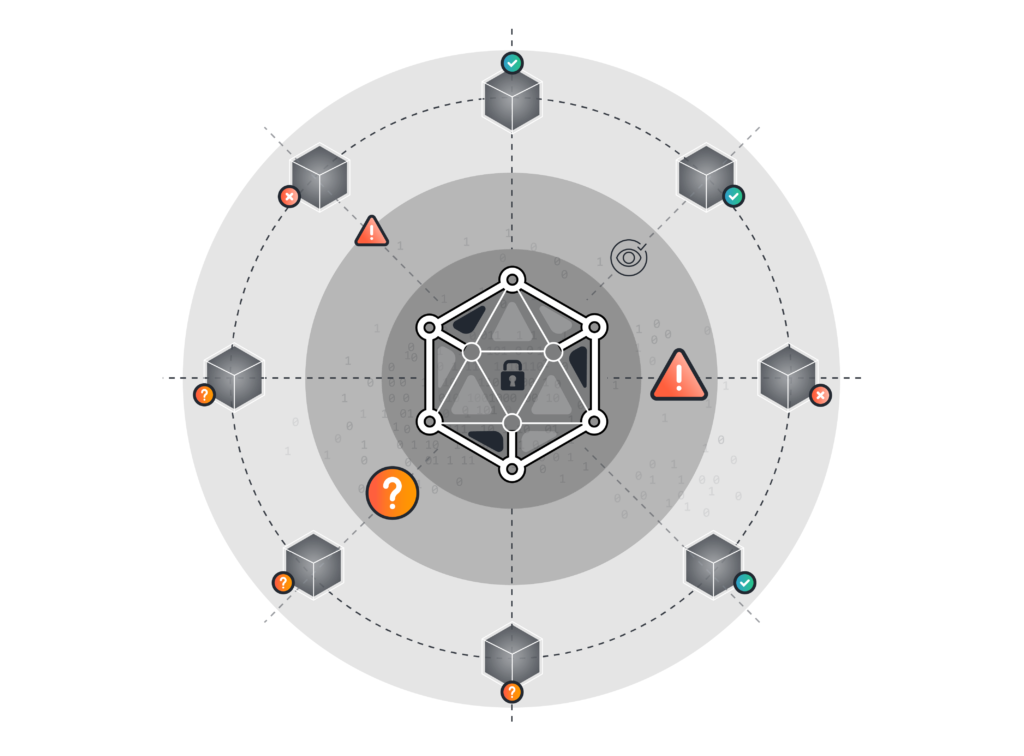
Gain complete visibility: Detect and identify all assets on the network that could open the door for an attack.
Minimize Risk: Isolate and disable shadow IT, unknown or orphaned assets, or any other potential entry points and attack vectors.
Manage your asset lifecycle: Set timely notifications to upgrade or replace aging infrastructure and software.
Integrate seamlessly: Fuel your IT security stack with Lansweeper’s always accurate asset data.
Discover all hardware, software, virtual assets, and user data across the expanding technology estate.
Pinpoint assets containing outdated software, misconfigurations and other vulnerabilities.
Use risk-based vulnerability assessment to determine the most important next step.
Know which assets to update, isolate, or replace, to eliminate vulnerabilities and reduce risk.
As technology expands to accommodate the hybrid workplace and increased digitization, the number of technology assets in the enterprise is growing exponentially. Unfortunately, this expands the cyber attack surface as well. Today, 43% of global organizations say the digital attack surface is “spiraling out of control.”
Enter Cyber Asset Attack Surface Management (CAASM). Despite enormous investments in security, most enterprises still don’t understand the attack surface – which means corporate networks are at risk. Leading security tools focus on threat detection and mitigation, not device discovery and recognition, and must rely on outdated and often inaccurate data.
To combat these challenges, organizations are spending more on cybersecurity tools to support the critical practice of Cyber Asset Attack Surface Management (CAASM). CAASM solutions help to identify all potentially vulnerable assets before an attacker can get in. Detecting and preventing attacks won’t be possible without complete and accurate technology asset data. Learn how Lansweeper enables CAASM by providing visibility and actionable data on your Technology Estate in this whitepaper.

Complete and up-to-date IT Asset data is a critical starting point for CAASM – first, you need to know what assets you have to protect them. Lansweeper makes it fast and easy to create a comprehensive technology asset inventory with detailed and granular data about all technology assets connected to the network, both local and remote.
Lansweeper’s advanced discovery and credential-free device recognition (CDR) technology automatically detect all network-connected assets – even rogue devices that only briefly touch the network, shadow IT, OT, and forgotten, idle devices – extracting data from the “bare metal,” creating an always-accurate IT asset inventory, regardless of the platform.

Lansweeper organizes and contextualizes technology asset data to make it actionable for a variety of business use cases. Pre-built and customizable dashboards help you understand patch status, vulnerability exposure, security compliance, software licensing, hardware warranty information and more. Leverage advanced reporting features to retrieve, analyze and share data as needed, or integrate Lansweeper with Microsoft Power BI to view complete and up-to-date technology asset data alongside other business data for a 360-degree view and improved cyber attack surface visibility.
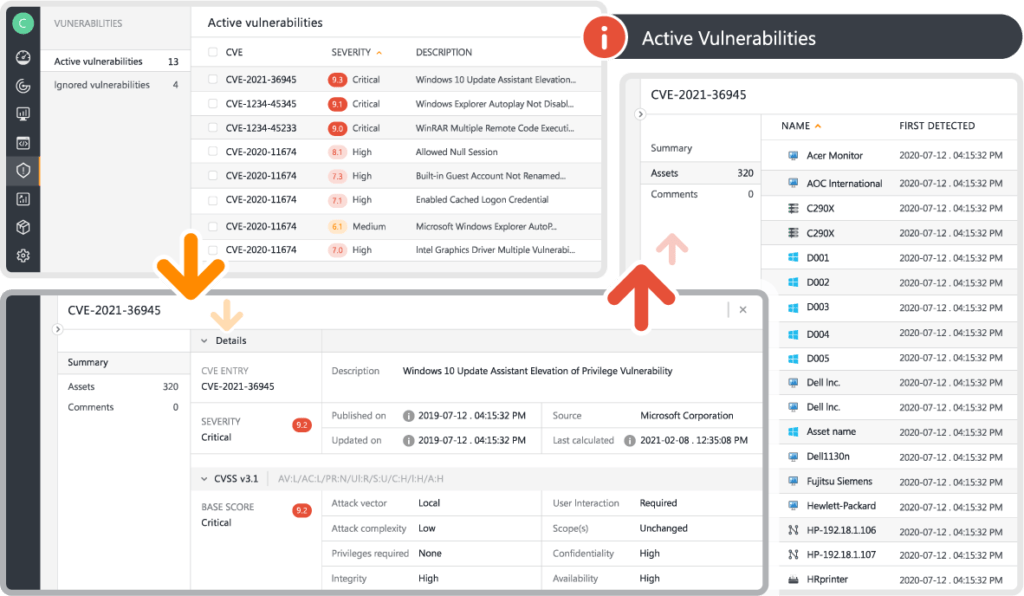
Stay on top of the latest vulnerabilities with Lansweeper’s pre-made or custom Vulnerability Reports. Expedite patches and updates, and gain information about the anti-virus status of your Windows machines. Lansweeper issues Patch Tuesday reports to ensure your network assets are updated with the latest Windows patches, as well. Plus, Lansweeper Sites‘ Automated Risk Insights provides a complete list of all known vulnerabilities in the NIST, CISA, and MS Vulnerability Databases, so you can quickly identify at-risk assets. The customizable list view lets you put the most useful information front and center. This way you can easily prioritize remediation activities for improved cyber attack surface management.
There is no single tool that can do it all, so we focus on what we do best – detecting, and identifying assets on the network. But, we are open and interoperable by design. Through our partnerships, Lansweeper seamlessly connects to operational systems across the technology stack, including CMDB, ITSM, SIEM/SOAR tools and others, ensuring they have access to the most up to date IT asset data at all times.
These integrations eliminate data silos and reduce operational overhead by simplifying the process of investigating and remediating security incidents. Lansweeper’s extensive API capabilities help customers and partners derive unique insights from Lansweeper data.
Explore all our features, free for 14 days.