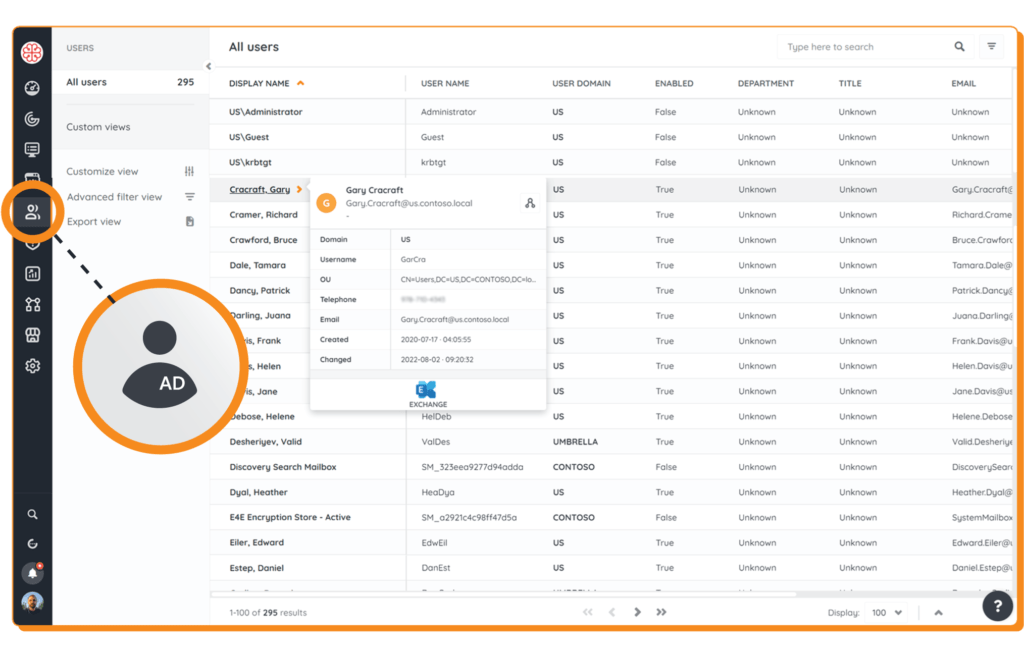
With Lansweeper, user inventory management is easy and straightforward. The first step is always to get a complete overview of your network and its users by scanning the network. Lansweeper does this automatically using a wide range of network protocols. When scanning your Active Directory, Lansweeper will scan all AD users and their properties, regardless of their status. Lansweeper scans are agentless, so you do not need to install it on every device you want to scan.
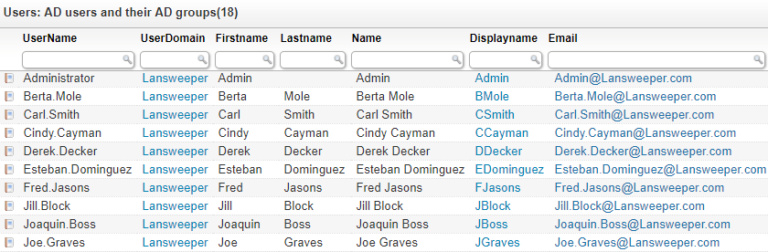
Once the network has been scanned, the data is securely stored and accessible through our user-friendly interface. Your user data is offered in an orderly overview so that you can instantly track user access and check user permissions. This overview includes local users, AD users, Azure AD Users, and assets. New pages will be created automatically for new users or assets with every following scan.
Lansweeper also scans Office 365. This means that the retrieved user data will automatically be unified with existing (Azure) Active Directory, allowing you to also manage Office 365 users. This means that whenever you view a user within Lansweeper, you cannot only see the (Azure) Active Directory Information, but also any related Office 365 information. You will very easily identify users who are missing licenses or plans, have unsafe passwords and much more.
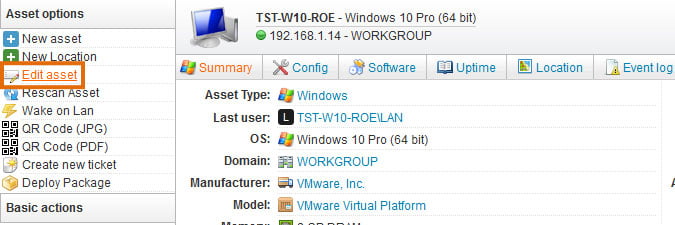
Once you have a comprehensive overview of your IT users and assets, Lansweeper offers built-in reports, or the possibility to create your own custom reports, to simplify analyzing the collected data. By linking users to the assets, you can easily track who is using which asset and navigate from asset pages to the related user and vice-versa. Establish relations for Local Users, (Azure) AD User Groups, and OUs. Better user-asset relations, lead to faster issue resolutions, better resource allocation, and a complete audit trail of devices that frequently change owners. View user permissions, AD information, and all the other information scanned from the assets, like event log data from your Windows devices. In fact, event logs contain user events that Lansweeper can easily retrieve and report on.

“One of my favorite reports is ‘Unauthorized Local Administrators‘. I am a stickler when it comes to this and want to know immediately when a tier has created a local admin on a PC that they should not have.”
The obtained overview allows you to actively manage users. You can revoke permissions, remove software (remotely) or perform other changes with the use of Lansweeper’s actions and deployment packages. Actions are built-in but can also be customized. You can create any user action you require. To see what kind of custom actions have already been made by Lansweeper users, you can check out the forum. By combining the data retrieved with the unlimited possibilities of custom actions and deployments, Lansweeper provides the most reliable platform for user management.
Unauthorized administrators can be a threat to your network. When you grant local admin rights, you risk the installation of unapproved software, breaking business-critical applications and causing disruption and downtime. In order to minimize this risk, Lansweeper offers you an easy method of finding local administrators. For a system administrator, it is often important to know which accounts have administrative privileges on the computers they manage. The reports tab in Lansweeper’s web console even has a built-in report called “Unauthorized Administrators“. These users are not limited in what they can do with the account and can therefore be a severe security threat to your IT network.
Your AD user data is now also available in Lansweeper Sites and in a more convenient form than ever. The User Inventory feature gives you a full view of all AD users in your network, connected users, and their details. Like all list views in Sites, the User Inventory view is customizable, has advanced filters, and can be exported to CSV or Excel. It has its own local search, but user pages will also show up in your global search. The enhanced access controls in Lansweeper Sites allow you to manage and monitor who has access to your user data. This allows you to remain compliant with data security policies. This initial release is just the beginning. We’re committed to ongoing enhancements and improvements based on user feedback. Stay tuned for exciting updates on the horizon!
User management is the process of inventorying all users and their access rights to resources or information within a computer network. It also involves maintaining an up-to-date identity inventory. User management is usually done by an IT administrator who can provide or deny users’ access. The admin does this by using a user management system.
User management not only greatly enhances productivity among users of your IT network, it is also essential for security reasons. You want to know who has access to your network resources. An unidentified user can be a cybercriminal looking for access to your critical data. But you cannot identify or even find unauthorized users without a system that can scan your entire network. That is why IT admins use a solution like Lansweeper.
Discover Assets You Don’t Even Know About & Eliminate Network Blind Spots.