⚡ TL;DR | Go Straight to the Fortinet Vulnerability Audit Report
Fortinet has released a security advisory detailing a critical stack-based overflow vulnerability in FortiOS and FortiProxy. If successfully exploited the flaw could allow a remote attacker to execute arbitrary code on targetted devices. This can in turn compromise the the integrity of sensitive data and files. We have added a new report to Lansweeper to help you locate vulnerable devices.
Fortinet Vulnerability CVE-2023-33308
The vulnerability tracked as CVE-2023-33308 is a stack-based overflow vulnerability in FortiOS and FortiProxy and received a critical CVSS score of 9.8. An attacker could use this flaw to execute malicious code by sending specially crafted packages that exceed the buffer’s capacity to overwrite critical memory parameters relating to functions. Arbitrary code execution attacks can compromise the integrity of sensitive data and files. You can read the full details in Fortinet’s advisory.
Update Vulnerable Fortinet Devices
Fortinet says in their security advisory that this vulnerability had already been resolved in a previous release, without a corresponding PSIRT Advisory. This means that the latest release branch, FortiOS 7.4 is not affected. You can find a list of the impacted versions below, as well as the fixed versions. Make sure to update any affected devices as soon as possible.
If it is not possible for you to update right away, you can HTTP/2 support on SSL inspection profiles used by proxy policies or firewall policies with proxy mode. You can find an example with custom-deep-inspection profile in the advisory.
| Affected version | Fixed version |
| FortiOS version 7.2.0 through 7.2.3 | FortiOS version 7.2.4 or above |
| FortiOS version 7.0.0 through 7.0.10 | FortiOS version 7.0.11 or above |
| FortiProxy version 7.2.0 through 7.2.2 | FortiProxy version 7.2.3 or above |
| FortiProxy version 7.0.0 through 7.0.9 | FortiProxy version 7.0.10 or above |
This vulnerability does not impact FortiOS products from the 6.0, 6.2, 6.4, 2.x, and 1.x release branches.
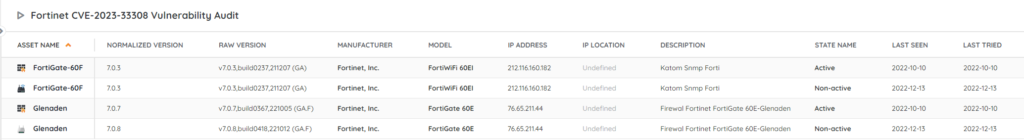
Discover Vulnerable Fortinet Devices
To help you locate vulnerable Fortinet devices, our technical team has put together a new report. This way you have an actionable list of devices that are running an affected version and need you to take action. You can get the report via the link below.