Pro Tips with Esben #14
Back in June 2021, in response to a Windows DCOM server security feature bypass vulnerability, Microsoft introduced DCOM Hardening. In this blog, we will take a look at how it can affect you and how you can prepare for the upcoming changes Microsoft will implement.
Distributed Component Object Model
Starting with some background information, Distributed Component Object Model or DCOM is a protocol used for exposing application objects using remote procedure calls (RPCs). DCOM is used for communication between the software components of networked devices. DCOM is very widely used by network devices and software alike.
The Origin Story – CVE-2021-26414
Back in June of 2021, CVE-2021-26414, a Windows DCOM server security feature bypass vulnerability with a CVSS score of 4.8 was disclosed and a partial fix was released by Microsoft.
“Installing the security updates released on June 8, 2021, enables client-side protections in a pure Windows environment but does not provide any protection in environments with non-windows DCOM client”
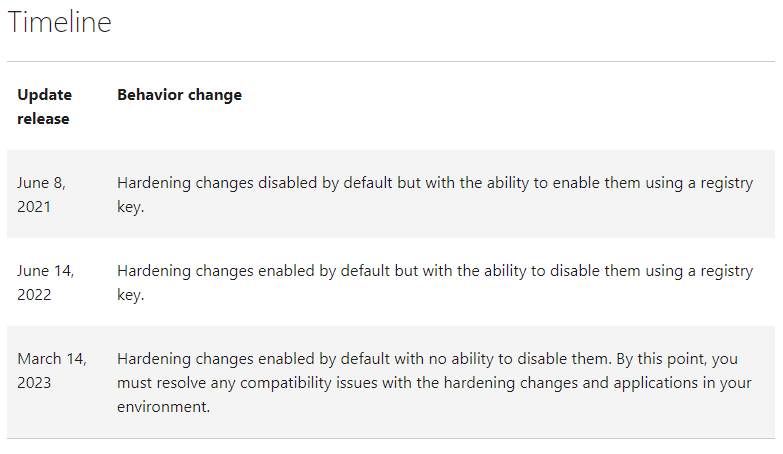
As part of the process to fully fix this vulnerability, three stages were created to fully fix the issue over time. This was put in place to give admins time to identify and mitigate issues between Windows and non-Windows operating systems and applications that rely on DCOM.
DCOM Hardening Impact
DCOM hardening and fixing a vulnerability all sounds great. But the effect of this change can be quite significant depending on how many devices in your IT environment rely on DCOM and don’t support the new DCOM hardening. This means that potentially any device, service, or application you have running that relies on DCOM to communicate could stop working on March 14, 2023. Think of all the PLCs, fire alarm systems, climate control systems, software that relies on DCOM that just stops providing data.
Luckily, we’ve already performed tests for Lansweeper, and no compatibility issues have been found. You’ll notice no change in Lansweeper behavior once DCOM hardening is implemented. However, other publishers or manufacturers might not be so proactive.
Microsoft has provided some tools to find out if you’ll be running into issues before March 14. To test DCOM hardening, you can already enable it in Windows by creating the following registry key.
- Path : HKEY_LOCAL_MACHINESOFTWAREMicrosoftOleAppCompat
- Value Name: “RequireIntegrityActivationAuthenticationLevel”
- Type: dword
- Value Data: default = 0x00000000 means disabled. 0x00000001 means enabled. If this value is not defined, it will default to disabled.
To give you a better overview, I’ve also created a report that provides you with an overview of all Windows devices where the registry key has been detected, so you know exactly where DCOM hardening has been enabled or disabled.
Microsoft created three new error events to allow admins to identify where issues occur for the following Windows versions.
| Windows version | Available on or after these dates |
|---|---|
| Windows Server 2022 | September 27, 2021 KB5005619 |
| Windows 10, version 2004, Windows 10, version 20H2, Windows 10, version 21H1 | September 1, 2021 KB5005101 |
| Windows 10, version 1909 | August 26, 2021 KB5005103 |
| Windows Server 2019, Windows 10, version 1809 | August 26, 2021 KB5005102 |
| Windows Server 2016, Windows 10, version 1607 | September 14, 2021 KB5005573 |
| Windows Server 2012 R2 and Windows 8.1 | October 12, 2021 KB5006714 |
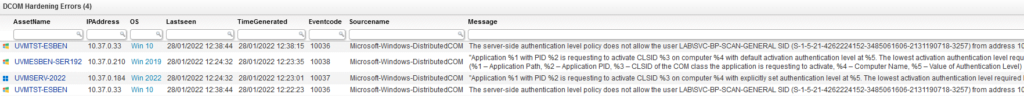
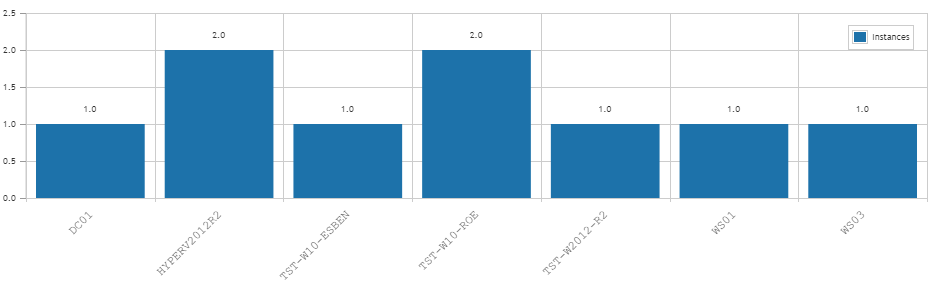
For server events, Event ID 10036 has been created. For client events, Event ID 10037 and 10038 have been added. Luckily, you won’t have to manually dig through the event log. As long as you’ve got Lansweeper running and scanning the event log, you’ll be able to run the report below to get an overview of all occurrences of the event and a chart that shows which device is running into how many errors.