PrintNightmare Vulnerability Audit
Operating System Security VulnerabilityFind Domain Controllers and Workstations Vulnerable to PrintNightmare
Microsoft accidentally released details of a critical unpatched vulnerability. The vulnerability CVE-2021-1675 that affects the Print Spooler service was supposed to be fixed in the last Patch Tuesday, but Microsoft recently updated the vulnerability and researchers found additional methods to exploit the vulnerability and there is no patch available yet. It is therefore critical that you take action as soon as possible and disable the Print Spooler service on all domain controllers while we all wait for a patch release from Microsoft.
The PrintNightmare vulnerability allows attackers to obtain full SYSTEM privileges by using a normal domain user account. Additionally, it can also lead to remote code execution with the highest privileges. You can read more about the vulnerability in our PrintNightmare blog post.
The report below provides an overview of all your devices, servers and workstation, and their patch status. Additionally, it shows the status of the Windows Print Spooler service, the start mode of the service, and the current status. Lastly, it also shows whether either of the registry keys that make a device vulnerable exists or are enabled. You can find more info on the fix on Microsoft’s official page.
Update July 7: Updates for Windows 10 versions added.
Update July 8: Updates for Windows 10 version 1607, Windows Server 2016, or Windows Server 2012 have been added.
Update July 13: PointAndPrint registry keys check added. Patch Tuesday July 2021 updates added.
The following registry key must be added to your custom registry scanning configuration to get accurate results in your report:
Rootkey: HKEY_LOCAL_MACHINE
Regpath: SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
Regvalue 1: NoWarningNoElevationOnInstall
Regvalue 2: UpdatePromptSettings
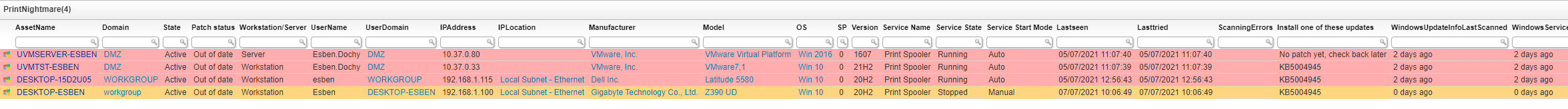
PrintNightmare Vulnerability Query
Select Distinct Top 1000000 Coalesce(tsysOS.Image,
tsysAssetTypes.AssetTypeIcon10) As icon,
tblAssets.AssetID,
tblAssets.AssetName,
tblAssets.Domain,
tblState.Statename As State,
Case tblAssets.AssetID
When SubQuery1.AssetID Then 'Up to date'
Else 'Out of date'
End As [Patch status],
Case
When tblComputersystem.Domainrole > 1 Then 'Server'
Else 'Workstation'
End As [Workstation/Server],
tblAssets.Username,
tblAssets.Userdomain,
tblAssets.IPAddress,
tsysIPLocations.IPLocation,
tblAssetCustom.Manufacturer,
tblAssetCustom.Model,
tsysOS.OSname As OS,
tblAssets.SP,
Case
When tsysOS.OScode Like '10.0.10240%' Then '1507'
When tsysOS.OScode Like '10.0.10586%' Then '1511'
When tsysOS.OScode Like '10.0.14393%' Then '1607'
When tsysOS.OScode Like '10.0.15063%' Then '1703'
When tsysOS.OScode Like '10.0.16299%' Then '1709'
When tsysOS.OScode Like '10.0.17134%' Then '1803'
When tsysOS.OScode Like '10.0.17763%' Then '1809'
When tsysOS.OScode Like '10.0.18362%' Then '1903'
When tsysOS.OScode Like '10.0.18363%' Then '1909'
When tsysOS.OScode Like '10.0.19041%' Then '2004'
When tsysOS.OScode Like '10.0.19042%' Then '20H2'
When tsysOS.OScode Like '10.0.19043%' Then '21H2'
End As Version,
Service.[Service Name],
Service.[Service State],
Service.[Service Start Mode],
Case
When SubQuery2.[NoWarningNoElevationOnInstall Vulnerable] Is Null Then 'No'
Else SubQuery2.[NoWarningNoElevationOnInstall Vulnerable]
End As [NoWarningNoElevationOnInstall Vulnerable],
Case
When SubQuery3.[UpdatePromptSettings Vulnerable] Is Null Then 'No'
Else SubQuery3.[UpdatePromptSettings Vulnerable]
End As [UpdatePromptSettings Vulnerable],
tblAssets.Lastseen,
tblAssets.Lasttried,
Case
When tblErrors.ErrorText Is Not Null Or
tblErrors.ErrorText != '' Then
'Scanning Error: ' + tsysasseterrortypes.ErrorMsg
Else ''
End As ScanningErrors,
Case
When tblAssets.AssetID = SubQuery1.AssetID Then ''
Else Case
When tsysOS.OSname = 'Win 2008' Then
'KB4457244, KB5004959, KB5004305, KB5004299'
When tsysOS.OSname = 'Win 7' Or tsysOS.OSname = 'Win 7 RC' Or
tsysOS.OSname = 'Win 2008 R2' Then
'KB5004953, KB5004951, KB5004289, KB5004307'
When tsysOS.OSname = 'Win 2012' Or
tsysOS.OSname = 'Win 8' Then
'KB5004956, KB5004960, KB5004294, KB5004302'
When tsysOS.OSname = 'Win 8.1' Or
tsysOS.OSname = 'Win 2012 R2' Then
'KB5004954, KB5004958, KB5004298, KB5004285'
When tsysOS.OScode Like '10.0.10240' Then 'KB5004950, KB5004249'
When tsysOS.OScode Like '10.0.10586' Then
'EOL, update to a higher Windows version'
When tsysOS.OScode Like '10.0.14393' Or
tsysOS.OSname = 'Win 2016' Then 'KB5004948, KB5004238'
When tsysOS.OScode Like '10.0.15063' Then
'EOL, update to a higher Windows version'
When tsysOS.OScode Like '10.0.16299' Then
'EOL, update to a higher Windows version'
When tsysOS.OScode Like '10.0.17134' Then
'EOL, update to a higher Windows version'
When tsysOS.OScode Like '10.0.17763' And tblOperatingsystem.Caption Not
Like '%LTSC%' Then 'EOL, update to a higher Windows version'
When tsysOS.OScode Like '10.0.17763' And tblOperatingsystem.Caption Like
'%LTSC%' Then 'KB5004947, KB5004244'
When tsysOS.OSname = 'Win 2019' Then 'KB5004947, KB5004244'
When tsysOS.OScode Like '10.0.18362' Then
'EOL, update to a higher Windows version'
When tsysOS.OScode Like '10.0.18363' Then 'KB5004946, KB5004245'
When tsysOS.OScode Like '10.0.19041' Then 'KB5004945, KB5004237'
When tsysOS.OScode Like '10.0.19042' Then 'KB5004945, KB5004237'
When tsysOS.OScode Like '10.0.19043' Then 'KB5004945, KB5004237'
End
End As [Install one of these updates],
Convert(nvarchar,DateDiff(day, QuickFixLastScanned.QuickFixLastScanned,
GetDate())) + ' days ago' As WindowsUpdateInfoLastScanned,
Convert(nvarchar,DateDiff(day, ServiceLastScanned.ServicesLastScanned,
GetDate())) + ' days ago' As WindowsServiceInfoLastScanned,
Case
When Convert(nvarchar,DateDiff(day, QuickFixLastScanned.QuickFixLastScanned,
GetDate())) > 3 Then
'Windows update information may not be up to date. We recommend rescanning this machine.'
Else ''
End As Comment,
Case
When tblAssets.AssetID = SubQuery1.AssetID And
((SubQuery2.[NoWarningNoElevationOnInstall Vulnerable] Is Null Or
SubQuery2.[NoWarningNoElevationOnInstall Vulnerable] <> 'Yes') And
(SubQuery3.[UpdatePromptSettings Vulnerable] Is Null Or
SubQuery3.[UpdatePromptSettings Vulnerable] <> 'Yes')) Then '#d4f4be'
When Service.[Safe/Vulnerable] = 'Safe' And
((SubQuery2.[NoWarningNoElevationOnInstall Vulnerable] Is Null Or
SubQuery2.[NoWarningNoElevationOnInstall Vulnerable] <> 'Yes') And
(SubQuery3.[UpdatePromptSettings Vulnerable] Is Null Or
SubQuery3.[UpdatePromptSettings Vulnerable] <> 'Yes')) Then '#FFD580'
Else '#ffadad'
End As backgroundcolor
From tblAssets
Inner Join tblAssetCustom On tblAssets.AssetID = tblAssetCustom.AssetID
Inner Join tsysAssetTypes On tsysAssetTypes.AssetType = tblAssets.Assettype
Inner Join tblOperatingsystem On tblOperatingsystem.AssetID =
tblAssets.AssetID
Inner Join tblState On tblState.State = tblAssetCustom.State
Inner Join tblComputersystem On tblAssets.AssetID = tblComputersystem.AssetID
Left Join tsysOS On tsysOS.OScode = tblAssets.OScode
Left Join (Select Top 1000000 tblQuickFixEngineering.AssetID
From tblQuickFixEngineering
Inner Join tblQuickFixEngineeringUni On tblQuickFixEngineeringUni.QFEID =
tblQuickFixEngineering.QFEID
Where tblQuickFixEngineeringUni.HotFixID In ('KB5004950', 'KB5004947',
'KB5004946', 'KB5004945', 'KB5004954', 'KB4457244', 'KB5004958',
'KB5004959', 'KB5004953', 'KB5004951', 'KB5004956', 'KB5004960',
'KB5004948', 'KB5004305', 'KB5004299', 'KB5004289', 'KB5004307',
'KB5004294', 'KB5004302', 'KB5004298', 'KB5004285', 'KB5004249',
'KB5004238', 'KB5004244', 'KB5004245', 'KB5004237')) As SubQuery1 On
tblAssets.AssetID = SubQuery1.AssetID
Left Join tsysIPLocations On tblAssets.IPNumeric >= tsysIPLocations.StartIP
And tblAssets.IPNumeric <= tsysIPLocations.EndIP
Left Join (Select Distinct Top 1000000 TsysLastscan.AssetID As ID,
TsysLastscan.Lasttime As QuickFixLastScanned
From TsysWaittime
Inner Join TsysLastscan On TsysWaittime.CFGCode = TsysLastscan.CFGcode
Where TsysWaittime.CFGname = 'QUICKFIX') As QuickFixLastScanned On
tblAssets.AssetID = QuickFixLastScanned.ID
Left Join (Select Distinct Top 1000000 tblErrors.AssetID As ID,
Max(tblErrors.Teller) As ErrorID
From tblErrors
Group By tblErrors.AssetID) As ScanningError On tblAssets.AssetID =
ScanningError.ID
Left Join tblErrors On ScanningError.ErrorID = tblErrors.Teller
Left Join tsysasseterrortypes On tsysasseterrortypes.Errortype =
tblErrors.ErrorType
Left Join (Select Distinct Top 1000000 TsysLastscan.AssetID As ID,
TsysLastscan.Lasttime As ServicesLastScanned
From TsysWaittime
Inner Join TsysLastscan On TsysWaittime.CFGCode = TsysLastscan.CFGcode
Where TsysWaittime.CFGname = 'SERVICES') As ServiceLastScanned On
tblAssets.AssetID = ServiceLastScanned.ID
Left Join (Select Top 1000000 tblAssets.AssetID,
Case
When (tblServiceStartMode.StartMode = 'Manual' Or
tblServiceStartMode.StartMode = 'Disabled') And
tblServiceState.State = 'Stopped' Then 'Safe'
Else 'Vulnerable'
End As [Safe/Vulnerable],
tblServicesUni.Caption As [Service Name],
tblServicesUni.Pathname As [Service Path],
tblServiceStartMode.StartMode As [Service Start Mode],
tblServiceState.State As [Service State]
From tblAssets
Inner Join tblAssetCustom On tblAssets.AssetID = tblAssetCustom.AssetID
Inner Join tblState On tblState.State = tblAssetCustom.State
Inner Join tblServices On tblServices.AssetID = tblAssets.AssetID
Inner Join tblServicesUni On tblServicesUni.ServiceuniqueID =
tblServices.ServiceuniqueID
Inner Join tblServiceStartMode On tblServiceStartMode.StartID =
tblServices.StartID
Inner Join tblServiceState On tblServiceState.StateID =
tblServices.StateID
Where tblServicesUni.Pathname Like '%spoolsv%' And tblState.Statename =
'Active') As Service On Service.AssetID = tblAssets.AssetID
Left Join (Select Top 1000000 tblRegistry.AssetID,
Case
When tblRegistry.Valuename Is Not Null And tblRegistry.Valuename <> ''
Then 'No'
When tblRegistry.Valuename Like '%NoWarningNoElevationOnInstall%' And
tblRegistry.Value = 1 Then 'Yes'
Else 'No'
End As [NoWarningNoElevationOnInstall Vulnerable]
From tblRegistry
Where
tblRegistry.Regkey Like
'%SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint'
And tblRegistry.Valuename Like '%NoWarningNoElevationOnInstall%')
SubQuery2 On SubQuery2.AssetID = tblAssets.AssetID
Left Join (Select Top 1000000 tblRegistry.AssetID,
Case
When tblRegistry.Valuename Is Not Null And tblRegistry.Valuename <> ''
Then 'No'
When tblRegistry.Valuename Like '%UpdatePromptSettings%' And
tblRegistry.Value = 1 Then 'Yes'
Else 'No'
End As [UpdatePromptSettings Vulnerable]
From tblRegistry
Where
tblRegistry.Regkey Like
'%SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint'
And tblRegistry.Valuename Like '%UpdatePromptSettings%') SubQuery3 On
SubQuery3.AssetID = tblAssets.AssetID
Where tsysOS.OSname <> 'Win 2000 S' And tsysOS.OSname Not Like '%XP%' And
tsysOS.OSname Not Like '%2003%' And (Not tsysOS.OSname Like 'Win 7%'
Or Not tblAssets.SP = 0) And tblAssetCustom.State = 1 And
tsysAssetTypes.AssetTypename Like 'Windows%'
Order By tblAssets.Domain,
tblAssets.AssetName