⚡ TL;DR | Go Straight to the VMware Vulnerability Report
VMware has released security patches for vCenter Server and ESXi to address two vulnerabilities, the one in vCenter Server being the most severe. Exploiting the vulnerability, an attacker could execute arbitrary code on the underlying OS that hosts the vCenter Server. This would allow an attacker to access and modify, delete, or even steal sensitive data.
vCenter Server Vulnerability CVE-2022-31680
The vulnerability tracked as CVE-2022-31680 affects vCenter Server and is an unsafe deserialization vulnerability in the PSC. It has received a CVSSv3 base score of 7.2. A malicious actor with admin access to a vCenter Server could use the vulnerability to execute arbitrary code on the underlying operating system that hosts the vCenter Server. There are no known workarounds but the issue only impacts vCenter Server 6.5 with an external PSC. You are advised to update any at-risks installations as soon as possible. You can find more information about the security patch in VMware’s release notes.
VMware ESXi Vulnerability CVE-2022-31681
The null-pointer dereference vulnerability tracked as CVE-2022-31681 affects ESXi versions 6.5, 6.7, and 7.0. It has a low severity rating with a maximum CVSSv3 base score of 3.8, however, you are still advised to update any installations as soon as possible. An attacker with privileges within the VMX process could use the vulnerability to create a denial of service condition on the host. You can find more information regarding the security patches in their respective release notes:
- VMware ESXi 6.5, Patch Release ESXi650-202210001
- VMware ESXi 6.7, Patch Release ESXi670-202210001
- VMware ESXi 7.0 Update 3f Release Notes
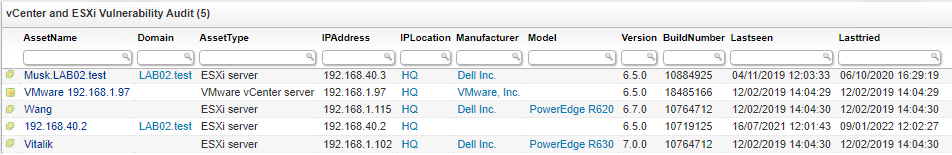
Discover Vulnerable vCenter Server and ESXi Installations
To find any installation of vCenter Server or ESXi in your network that may be vulnerable to the vulnerabilities listed above, our team at Lansweeper has created a dedicated vulnerability report. This way you have an actionable list of devices that may need an update with the latest security patches
The vulnerability report is automatically added to Lansweeper Cloud sites. Lansweeper Cloud is included in all our licenses without any additional cost and allows you to federate all your installations into one single view so all you need to do is look at a single report. Vulnerability reports are automatically added to Lansweeper Cloud.