
Lansweeper Vulnerability Audit Report Available
NVIDIA issued a security bulletin and update to fix five high and medium severity security issues in the NVIDIA GPU Display Driver that could lead to local code execution, escalation of privileges, and denial of service on vulnerable Windows computers. Sounds familiar? In May, three vulnerabilities in NVIDIA GeForce, Quadro, and Tesla graphics cards had been found and patched.
Important side note: All the security flaws require local user access and cannot be exploited remotely, with potential attackers having to rely on user interaction to execute malicious code designed to exploit one of the fixed bugs on machines with unpatched display drivers. The software security issues fixed by NVIDIA are listed below.
- CVE-2019-5683 – NVIDIA Windows GPU Display Driver contains a vulnerability in the user mode video driver trace logger component. When an attacker has access to the system and creates a hard link, the software does not check for hard link attacks. This behavior may lead to code execution, denial of service, or escalation of privileges.
- CVE-2019-5684 – NVIDIA Windows GPU Display Driver contains a vulnerability in DirectX drivers, in which a specially crafted shader can cause an out of bounds access of an input texture array, which may lead to denial of service or code execution.
- CVE-2019-5685 – NVIDIA Windows GPU Display Driver contains a vulnerability in DirectX drivers, in which a specially crafted shader can cause an out of bounds access to a shader local temporary array, which may lead to denial of service or code execution.
- CVE-2019-5686 – NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which the software uses an API function or data structure in a way that relies on properties that are not always guaranteed to be valid, which may lead to denial of service.
- CVE-2019-5687 – NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which an incorrect use of default permissions for an object exposes it to an unintended actor, which may lead to information disclosure or denial of service.
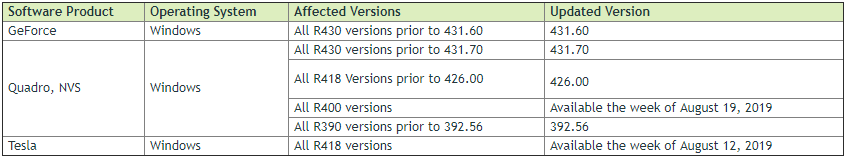
The table below lists the NVIDIA software products affected such as GeForce, Quadra, and Tesla, versions affected, and the updated versions that are included in this security update. You can download the updates from the NVIDIA Driver Downloads page.
VMware Out-of-Bounds Write Vulnerability
VMware published a security advisory reporting out-of-bounds read/write vulnerabilities in the pixel shader functionality for VMware ESXi, Workstation and Fusion.
The out-of-bounds write issue (CVE-2019-5684) can be exploited only if the host has an affected NVIDIA graphics driver. Successful exploitation of this issue may lead to code execution on the host. CVE-2019-5684 can be remediated by installing the updated NVIDIA graphics driver.
Find Vulnerable NVIDIA Versions in Your Network
If you currently have NVIDIA GPU Display Drivers deployed on your workstations, it’s pretty critical that you update it at the earliest opportunity to ensure that you don’t fall prey to this exploit.
Our custom NVIDIA vulnerability audit report can tell you in no time which devices have a vulnerable NVIDIA driver version in place and need to be patched.
If you haven’t already, start your free Lansweeper trial and get a report of all affected devices in no time.
Source: NVIDIA Security Bulletin



