VMware released its latest security advisory which contains 19 new vulnerabilities for all three currently supported versions 6.5, 6.7, and 7.0. The most critical vulnerability is an arbitrary file upload vulnerability in the Analytics service that requires immediate patching.
vCenter Server file upload vulnerability (CVE-2021-22005)
The most critical vulnerability is the file upload vulnerability. Rated with a CVSSv3 base score of 9.8, the vulnerability lies in the Analytics service. Any attacker with network access to port 443 on a vCenter Server is able to exploit this vulnerability and execute code on the vCenter Server by uploading a specially crafted file. While this specific vulnerability does not apply to vCenter Server 6.5, there are other vulnerabilities in this security advisory that do, so regardless of your version, it is important to update your vCenter Server to the latest version released on September 21, 2021.
It is not the first time VMware has had issues with its port 443 access to vCenter Servers. In May, it also had a critical remote code execution vulnerability that required the same port 443 access in order to exploit a vulnerability in the Virtual SAN Health Check plug-in.
Want to run this Audit Report?
Start your Free Lansweeper Trial to run the Audit Report.
Try for FreevCenter Server local privilege escalation vulnerability (CVE-2021-21991)
The second highest-rated vulnerability is a local privilege escalation vulnerability due to the way it handles session tokens and has a CVSSv3 base score of 8.8. By exploiting this vulnerability, an attacker with non-administrative user access on the vCenter Server host can gain Administrative privileges on the vSphere Client (HTML5) or vCenter Server vSphere Web Client (FLEX/Flash).
VMware has created a Q&A page for this specific vulnerability which has the most detailed information and most pressing questions you might have.
Manage Your vCenter Server Versions
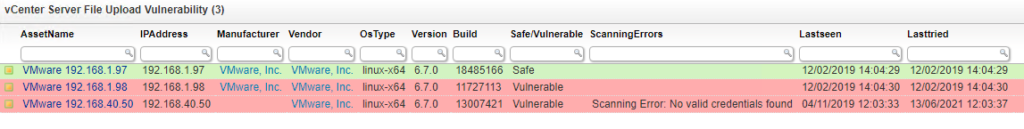
Alongside the two most critical vulnerabilities listed above, there are an additional 17 vulnerabilities that affect both VMware vCenter Server and VMware Cloud Foundation. The best way to manage your vCenter environment is by having a complete overview of it to begin with. To help you combat this vulnerability, we’ve created a special color-coded report which lists all of your vCenter Servers along with their version and build number so you know exactly which servers still require an update and which servers are safe.