⚡ TL;DR | Go Straight to the Barracuda ESG Vulnerability Audit Report
Barracuda Networks is urging all of its users to immediately replace all Email Security Gateway appliances impacted by the recently disclosed vulnerability CVE-2023-2868. It has recently come to light that the vulnerability has been exploited as a zero-day since at least October 2022. Barracuda originally started patching the appliances on May 19th, but on the 6th of June, they released another notice telling users to replace devices impacted by the exploitatoin, regardless of patch level. There are to date 3 known malware families exploiting the vulnerability. We have added new resources to Lansweeper to help you locate at-risk appliances.
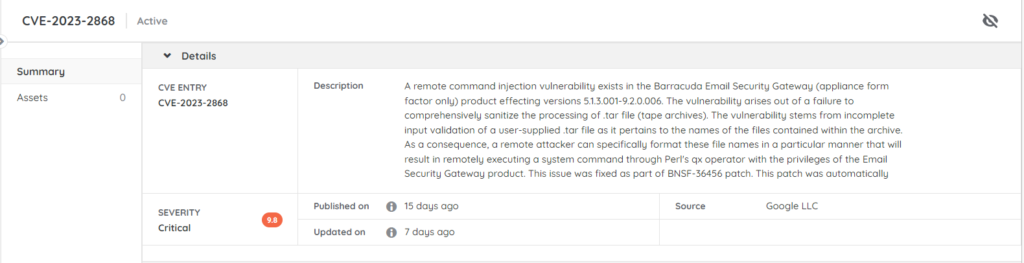
Barracuda ESG Vulnerability CVE-2023-2868
The vulnerability tracked as CVE-2023-2868 is a remote command injection vulnerability. It received a critical CVSS score of 9.8. A remote attacker could use it to format file names in a particular way that would result in remotely executing a system command through Perl’s qx operator with the privileges of the Email Security Gateway product. It seems that the flaw has already been exploited as a zero-day since October 2022 You can read the full details on Barracuda’s advisory page.
To date, 3 malware families have been identified that exploit this bug:
- SALTWATER is a trojanized module for the Barracuda SMTP daemon (bsmtpd) that contains backdoor functionality that allows it to upload or download arbitrary files, execute commands, as well as proxy and tunneling capabilities.
- SEASPY is an x64 ELF persistence backdoor that is activated by means of a “magic packet”.
- SEASIDE is a Lua based module for the Barracuda SMTP daemon (bsmtpd) that establishes reverse shells via SMTP HELO/EHLO commands sent via the malware’s command-and-control (C2) server.
Vulnerable Barracuda ESG Appliances
The Barracuda ESG vulnerability was initially discovered on May 19th and a patch was deployed a day later. It affects Barracuda ESG versions 5.1.3.001-9.2.0.006. A second fix went out on the 21st. If you have any ESG appliances of the affected versions, make sure to apply the patches and read through Barracuda’s security notice.
Key Findings
While the investigation is still ongoing, Barracuda has concluded the following as stated on their website:
- The vulnerability existed in a module that initially screens the attachments of incoming emails. No other Barracuda products, including our SaaS email security services, were subject to the vulnerability identified.
- The earliest identified evidence of exploitation of CVE-2023-2868 is currently October 2022.
- Barracuda identified that CVE-2023-2868 was used to obtain unauthorized access to a subset of ESG appliances.
- Malware was identified on a subset of appliances allowing for persistent backdoor access.
- Evidence of data exfiltration was identified on a subset of impacted appliances.
Replace Impacted Appliances
Barracuda is currently still investigating the exploitation of the bug. Users whose appliances are believed to be impacted will be notified through the user interface. If you receive such a notification you should immediately replace the impacted ESG, regardless of patch level. If you have not done so yet, reach out to Barracuda’s support team now at support@barracuda.com.
Discover Vulnerable Barracuda ESG Appliances
Our technical team has added new resources to Lansweeper to help you locate potentially vulnerable Barracuda ESG appliances in your network. This will give you an actionable list of devices that may still need to be patched. This way you can easily see which devices still require your intervention. You can find more information via the link below.