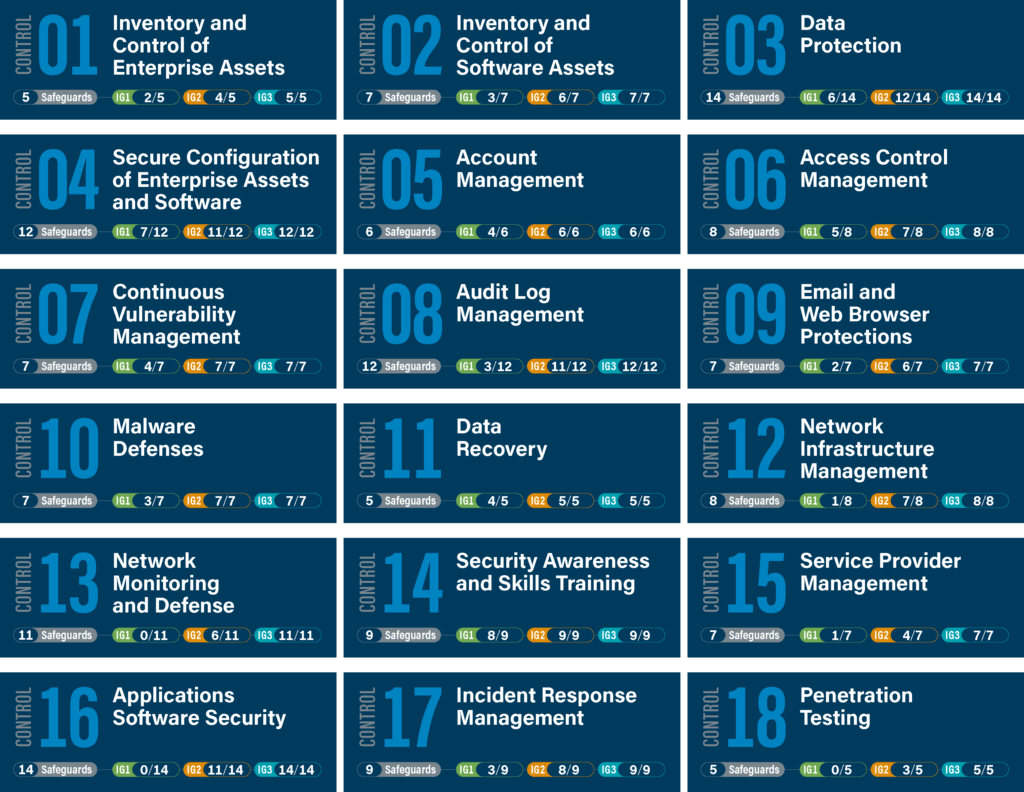
When companies struggle with what to do and how to demonstrate their Cyber Security efforts, many turn to ISO27001 & ISO27002. These frameworks are excellent for showing compliance but not well-suited for prioritizing, measuring and implementing practical IT-security initiatives. To that end, you need a consensus-based framework, such as the CIS 18 critical security controls®, which includes detailed practical and prioritized advice on how to implement cyber security. The CIS® controls include detailed instructions on what to do, how to measure, how to prioritize and how to audit your cybersecurity posture.
A well-maintained asset inventory is key in building a more comprehensive security program based on the CIS Critical Security Controls. As the controls are most effective when implemented in order, we have listed them below in order as well. The first two controls call for an Inventory of Hardware Software Assets and rely heavily on the IT asset inventory. This is where the benefits of Lansweeper, being at its core an ITAM solution, are the most obvious. However, Lansweeper can be used to support many of the other controls as well.
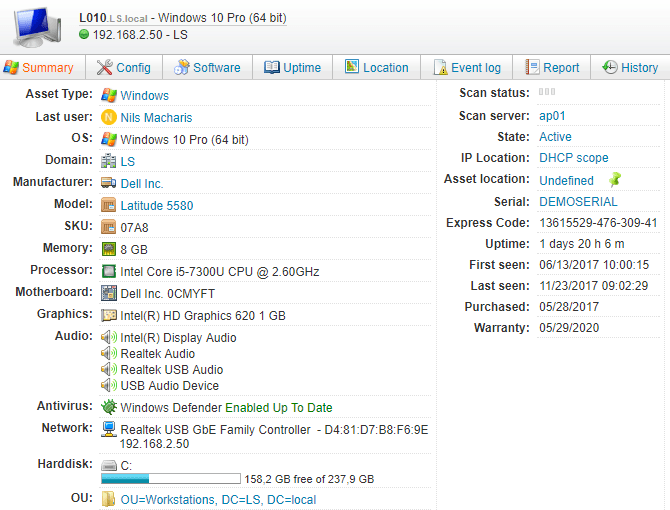
Lansweeper continuously detects hardware assets on your network and reports on changes, as well as newly discovered devices. Create an inventory of workstations, servers, network devices, non-computing/IoT devices, mobile devices, cloud assets, and OT Devices. The first CIS control guides you to implement a process of regularly, automatically discovering these assets and their details, then authorizing or removing unauthorized devices. Use Lansweeper’s many scanning methods like Active Directory scanning and the passive scanning of Asset Radar to get a complete inventory of any device connected to the network.
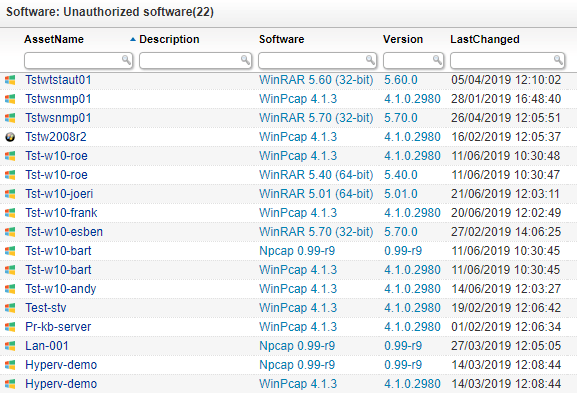
Lansweeper automatically discovers the software along with its version number, publisher, and install date on all your hardware assets. You must implement a process for removing unwanted software from your network thereby leaving only authorized software on authorized devices. Lansweeper’s out-of-the-box reports help to identify and mark software as “Allowed,” “Denied” or “Neutral”. Utilize the detailed software information to ensure only supported software is used in your IT environment.
Explore all our features, free for 14 days.