Microsoft Office “Follina” Zero-Day
Security Software VulnerabilityFind Devices Vulnerable to CVE-2022-30190
Microsoft released a new security advisory for CVE-2022-30190, a vulnerability in the Microsoft Support Diagnostic Tool. Microsoft summarizes the vulnerability as follows:
A remote code execution vulnerability exists when MSDT is called using the URL protocol from a calling application such as Word. An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application. The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights.
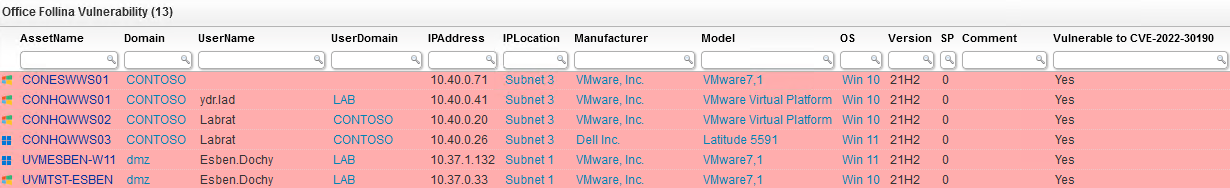
While there is no official fix yet, Microsoft has detailed how to prevent attackers from abusing the vulnerability with some registry key changes You can read more about the vulnerability in our Microsoft Office Vulnerability blog post. The audit below will give you a full overview of all your devices and whether the registry key that needs to be deleted has been detected, thus showing you if the devices are vulnerable or not.
Microsoft Office "Follina" Zero-Day Query
Select Top 1000000 tblAssets.AssetID, tblAssets.AssetName, tblAssets.Domain, tblAssets.Username, tblAssets.Userdomain, Coalesce(tsysOS.Image, tsysAssetTypes.AssetTypeIcon10) As icon, tblAssets.IPAddress, tsysIPLocations.IPLocation, tblAssetCustom.Manufacturer, tblAssetCustom.Model, tsysOS.OSname As OS, tblAssets.Version, tblAssets.SP, Case When TsysLastscan.Lasttime < GetDate() - 1 Then 'Last registry scan more than 24 hours ago! Information may not be up-to-date. Try rescanning this machine.' End As Comment, Case When SubQuery1.Value Is Not Null And SubQuery1.Value <> '' Then 'Yes' Else 'No' End As [Vulnerable to CVE-2022-30190], Case When tblErrors.ErrorText Is Not Null Or tblErrors.ErrorText != '' Then 'Scanning Error: ' + tsysasseterrortypes.ErrorMsg Else '' End As ScanningErrors, TsysLastscan.Lasttime As LastRegistryScan, SubQuery1.Lastchanged, tblAssets.Firstseen, tblAssets.Lastseen, tblAssets.Lasttried, Case When SubQuery1.Value Is Not Null And SubQuery1.Value <> '' Then '#ffadad' Else '#d4f4be' End As backgroundcolor From tblAssets Inner Join tblAssetCustom On tblAssets.AssetID = tblAssetCustom.AssetID Inner Join tsysAssetTypes On tsysAssetTypes.AssetType = tblAssets.Assettype Inner Join tsysIPLocations On tsysIPLocations.LocationID = tblAssets.LocationID Inner Join tblState On tblState.State = tblAssetCustom.State Left Join tsysOS On tsysOS.OScode = tblAssets.OScode Left Join (Select Distinct Top 1000000 tblErrors.AssetID As ID, Max(tblErrors.Teller) As ErrorID From tblErrors Group By tblErrors.AssetID) As ScanningError On tblAssets.AssetID = ScanningError.ID Left Join tblErrors On ScanningError.ErrorID = tblErrors.Teller Left Join tsysasseterrortypes On tsysasseterrortypes.Errortype = tblErrors.ErrorType Inner Join TsysLastscan On tblAssets.AssetID = TsysLastscan.AssetID Inner Join TsysWaittime On TsysWaittime.CFGCode = TsysLastscan.CFGcode Left Join (Select Top 1000000 tblRegistry.AssetID, tblRegistry.Regkey, tblRegistry.Valuename, tblRegistry.Value, tblRegistry.Lastchanged From tblRegistry Where tblRegistry.Regkey Like '%HKEY_CLASSES_ROOT\ms-msdt') SubQuery1 On SubQuery1.AssetID = tblAssets.AssetID Where tblAssetCustom.State = 1 And TsysWaittime.CFGname = 'registry' Order By tblAssets.Domain, tblAssets.AssetName