- Lansweeper Community
- Knowledge Center
- Knowledge Base
- Scanning your network
- Creating and mapping scanning credentials
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
12-08-2014
07:30 PM
- edited on
02-06-2024
12:05 PM
by
Nils
![]()
This page provides information on how to create and map scanning credentials for various types of devices and platforms in Lansweeper.
Lansweeper uses scanning credentials, which are login/password combinations and certificates/keys, to remotely access and scan network assets. The following assets require a scanning credential in order to be scanned remotely: Linux, Unix, Mac and Windows computers, VMware and vCenter servers, Citrix XenServers, network devices (printers, switches) that have SNMP enabled, AWS and Azure cloud assets, and Office 365 accounts. Windows computer credentials are also used when deploying packages on computers.
Your Lansweeper Classic installation allows you to submit an unlimited number of scanning credentials. Scanning credentials are managed in the following section of the web console: Scanning > Scanning Credentials.
- Airwatch
- AWS
- Azure
- Chrome OS
- Citrix
- Intune
- Office 365
- Microsoft Cloud Service to scan Office 365
- Microsoft Cloud Service to scan Intune
- SCCM
- SNMP (v1/v2)
- SNMP (v3)
- SSH
- SSH certificate
- vCenter
- VMware
- Windows
- AWS region
- Azure subscription ID
- IP address
- IP range
- Individual Windows computer
- Domain or workgroup
Creating scanning credentials
To create a credential, select Add new Credential in the Scanning > Scanning Credentials section of the web console. There are various types of credentials:
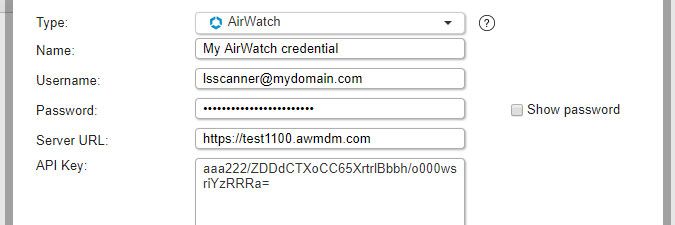
AirWatch credentials (added in Lansweeper 7.2)
- Used for scanning: Android, iOS (iPhone and iPad), Chrome OS and Windows Phone mobile devices enrolled in VMware AirWatch. When you submit an AirWatch credential, an AirWatch scanning target is automatically created as well.
- Must have: read-only access to the REST API in VMware Workspace ONE. Info on how to set this up can be found in this knowledge base article.
- Name: custom name you can assign to the credential.
- Username: your username in VMware Workspace ONE.
- Password: your user account's password.
- Server URL: your VMware Workspace ONE server URL.
- API key: API key with read access to the REST API in VMware Workspace ONE.
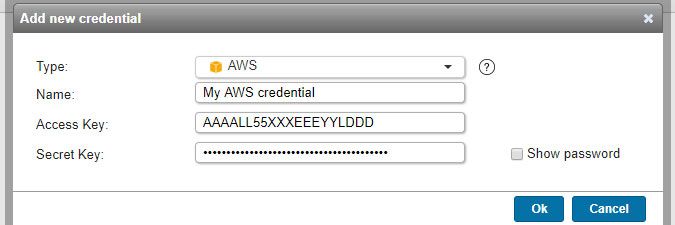
AWS credentials (added in Lansweeper 7.1)
- Used for scanning: AWS VPCs and instances.
- Must have: list-only programmatic access to your EC2-VPC environments. Info on how to set this up can be found in this knowledge base article.
- Name: custom name you can assign to the credential.
- Access key: access key ID of the user with list access to EC2.
- Secret key: secret access key of the user with list access to EC2.
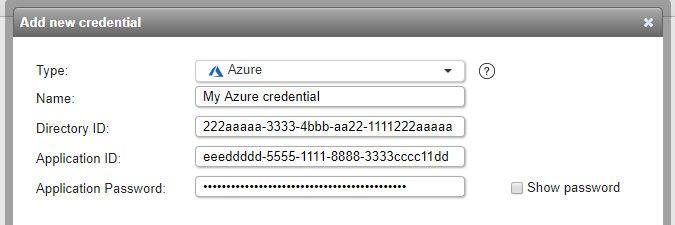
Azure credentials (added in Lansweeper 7.1)
- Used for scanning: Azure resource groups and virtual machines.
- Must have: read-only access to your Azure subscription. You must register an application in Azure Active Directory of the type Web App / API, generate a key for it and assign it the Reader role for your subscription. Info on how to set this up can be found in this knowledge base article.
- Name: custom name you can assign to the credential.
- Directory ID: your Azure Active Directory (tenant) ID.
- Application ID: ID of the application with read access to your subscription.
- Application password: password/key of the application with read access to your subscription.
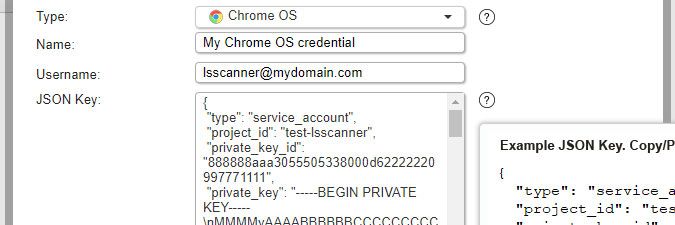
Chrome OS credentials (added in Lansweeper 7.2)
- Used for scanning: Chrome OS (e.g. Chromebook) machines. When you submit a Chrome OS credential, a Chrome OS scanning target is automatically created as well.
- Must have: read-only access to the Google Admin SDK API. Info on how to set this up can be found in this knowledge base article.
- Name: custom name you can assign to the credential.
- Username: email address of your Google account.
- JSON key: JSON key with read access to the Google Admin SDK API.
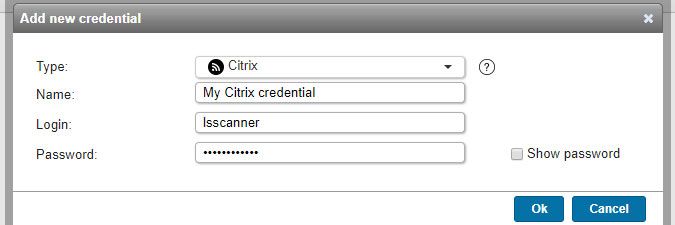
Citrix credentials (added in Lansweeper 7.0)
- Used for scanning: Citrix XenServers.
- Must have: access to XenAPI and be able to run the following command groups on your XenServers: delegating, drivers, locate, networking, processes, services, software, storage. Full root access is not required. Info on how to configure Citrix credentials can be found in this knowledge base article.
- Name: custom name you can assign to the credential.
- Login: your Citrix login.
- Password: your Citrix login's password.
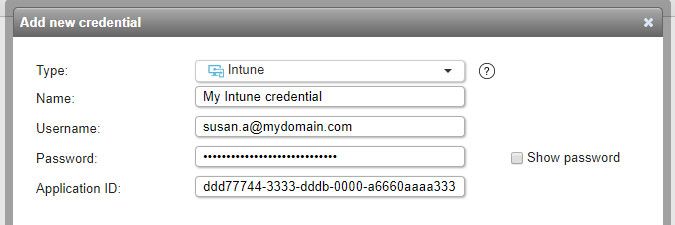
Intune credentials (added in Lansweeper 7.1)
- Used for scanning: Android, iOS (iPhone and iPad) and Windows Phone mobile devices enrolled in Microsoft Intune. When you submit an Intune credential, an Intune scanning target is automatically created as well.
- Must have: access to your Intune environment. You must register an application in Azure Active Directory of the type Native and grant it the DeviceManagementManagedDevices.Read.All permission under Microsoft Graph. Your user account must also have access to Intune. Info on how to set this up can be found in this knowledge base article.
- Name: custom name you can assign to the credential.
- Username: user with the ability to view devices in your Intune environment
- Password: user's password.
- Application ID: ID of the application with the DeviceManagementManagedDevices.Read.All permission.
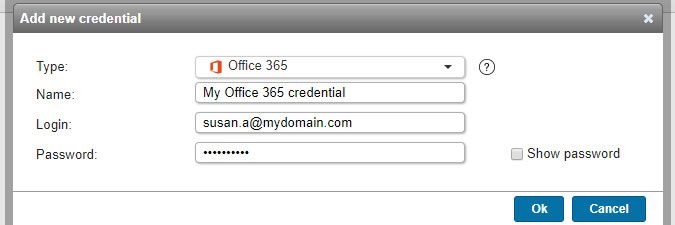
Office 365 credentials (added in Lansweeper 7.1)
- Used for scanning: Office 365 accounts. When you submit an Office 365 credential, an Office 365 scanning target is automatically created as well.
- Must have: administrative permissions to Office 365 to be able to inventory all contacts, mailboxes and ActiveSync devices. A global administrator is guaranteed to have sufficient rights.
- Name: custom name you can assign to the credential
- Login: user (email address) with administrative permissions to your Office 365 environment
- Password: user's password
Microsoft Cloud Service credential to scan your Office 365 data (added in Lansweeper 8.3)
- Used for scanning: Office 365 accounts with a Microsoft Graph application.
- Must have: administrative permissions to Office 365 to be able to inventory all contacts, mailboxes and ActiveSync devices. A global administrator is guaranteed to have sufficient rights.
- Name: custom name you can assign to the credential
- Application ID (obtained when creating the Microsoft Graph app in Azure)
- Directory ID (obtained when creating the Microsoft Graph app in Azure)
- Authentication type: either a client secret or a certificate thumbprint
- Create target for: When you check Create target for: Office 365 v2, an Office 365 v2 scanning target is automatically created as well.
Microsoft Cloud Service credential to scan your Intune data (added in Lansweeper 8.3)
- Used for scanning: Mobile devices enlisted in Intune with a Microsoft Graph application.
- Must have: access to your Intune environment. You must register an application in Azure Active Directory of the type Native and grant it the DeviceManagementManagedDevices.Read.All permission under Microsoft Graph. Your user account must also have access to Intune. Info on how to set this up can be found in this knowledge base article.
- Name: custom name you can assign to the credential
- Application ID (obtained when creating the Microsoft Graph app in Azure)
- Directory ID (obtained when creating the Microsoft Graph app in Azure)
- Authentication type: either a client secret or a certificate thumbprint
- Create target for: When you check Create target for: Intune v2, an Intune v2 scanning target is automatically created as well.
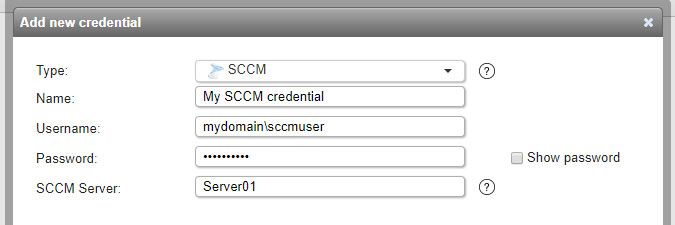
SCCM credentials (added in Lansweeper 7.2)
- Used for scanning: assets from your SCCM server's database. When you submit an SCCM credential, an SCCM scanning target is automatically created as well.
- Must have: local administrative permissions on the SCCM server and, at a minimum, the Read-Only Analyst security role within SCCM's Administrative Users.
- Name: custom name you can assign to the credential.
- Username: a down-level logon name like NetBIOS domain name\username (domain credentials) or a user principal name (UPN) like username@yourdomain.local (domain credentials) or .\username (local credentials) or username@outlook.com (Microsoft accounts).
- Password: your user account's password.
- SCCM server: name, IPv4 address or IPv6 address of an SMS Provider server in your SCCM environment.
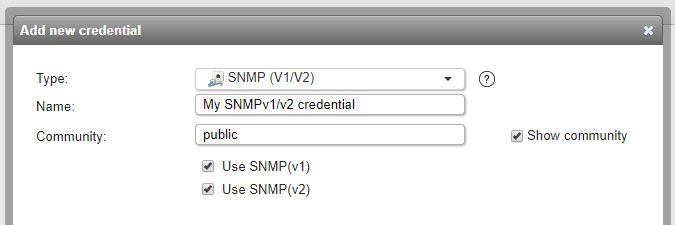
SNMP(v1/v2) credentials
- Used for scanning: network devices that have SNMPv1 or SNMPv2 enabled.
- Must have: read-only SNMP access to your devices.
- Name: custom name you can assign to the credential.
- Community: the (case-sensitive!) SNMP community string used by your devices. Many network devices use public and private as their default SNMP community strings, public being for read-only access and private for read/write access. Your devices could be using custom strings, however.
- Use SNMP(v1)/Use SNMP(v2): optionally, uncheck one of these boxes to have Lansweeper only try SNMPv1 or SNMPv2. Unchecking one of these boxes is generally only recommended if your devices have trouble processing SNMPv1 or SNMPv2 requests.
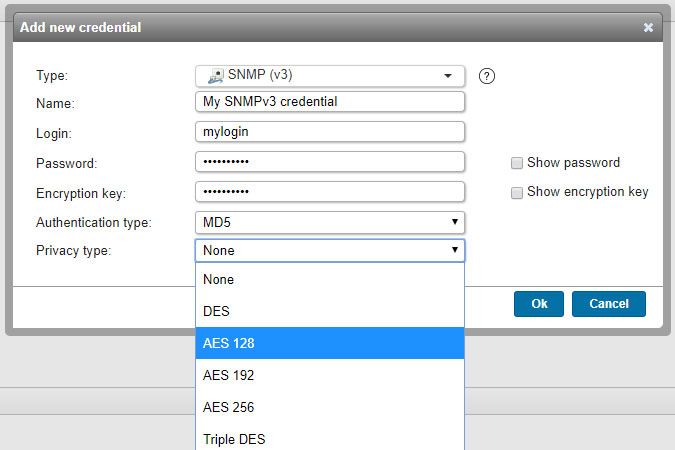
SNMP(v3) credentials
- Used for scanning: network devices that have SNMPv3 enabled.
- Must have: read-only SNMP access to your devices.
- Name: custom name you can assign to the credential.
- Login: your SNMP login.
- Password: your SNMP login's password.
- Encryption key: encryption key required if authentication type is set to MD5 or SHA1.
- Authentication type: None, MD5 or SHA1.
- Privacy type: None, DES, AES 128, AES 192, AES 256 or Triple DES.
- Context: optionally, context name of the SNMPv3 credential.
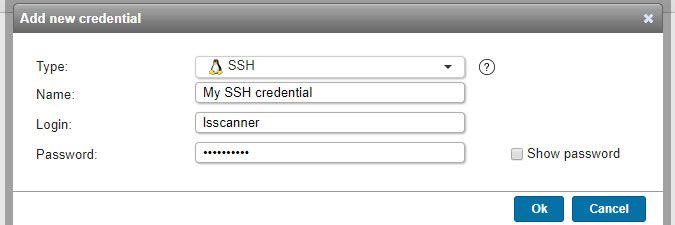
SSH credentials
- Used for scanning: Linux, Unix and Mac computers.
- Must have: access to the uname (Linux/Unix) or system_profiler (Mac) command. More info on Linux/Unix scanning requirements can be found in this knowledge base article and more info on Mac scanning requirements can be found in this knowledge base article.
- Name: custom name you can assign to the credential.
- Login: your SSH login.
- Password: your SSH login's password.
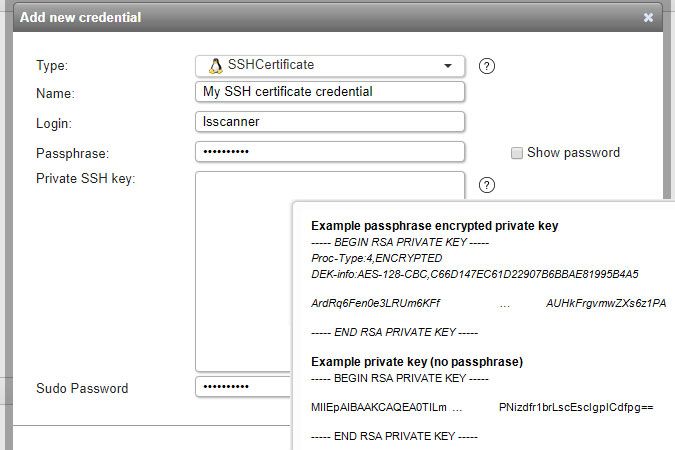
SSH certificate credentials
- Used for scanning: Linux and Unix computers.
- Must have: access to the uname command. More info on Linux/Unix scanning requirements can be found in this knowledge base article.
- Name: custom name you can assign to the credential.
- Login: your login.
- Passphrase: your passphrase, if there is one.
- Private SSH key: your SSH key. Sample inputs can be seen in the info pop-up when hovering over the question mark icon.
- Sudo Password: your sudo password.
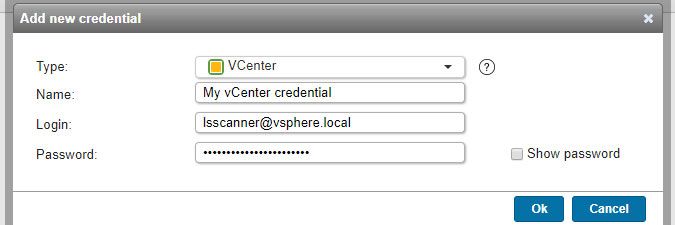
vCenter credentials (added in Lansweeper 7.0)
- Used for scanning: vCenter servers.
- Must have: read-only access to your vCenter servers. Info on how to set this up can be found in this knowledge base article.
- Name: custom name you can assign to the credential.
- Login: your vCenter login.
- Password: your vCenter login's password.
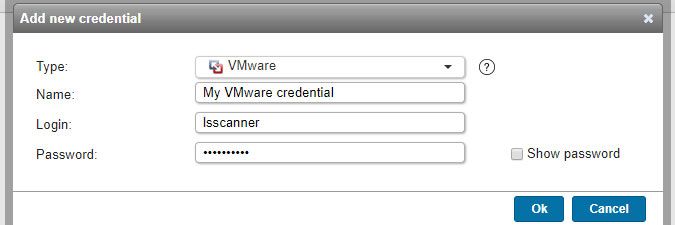
VMware credentials
- Used for scanning: VMware servers.
- Must have: read-only access to your ESXi servers.
- Name: custom name you can assign to the credential.
- Login: your VMware login.
- Password: your VMware login's password.
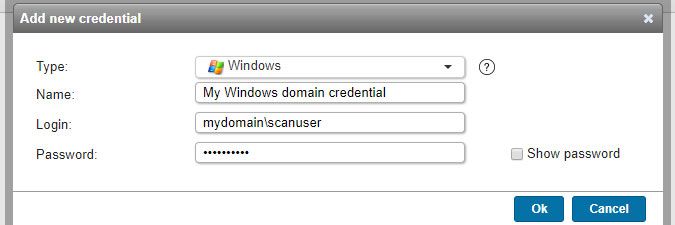
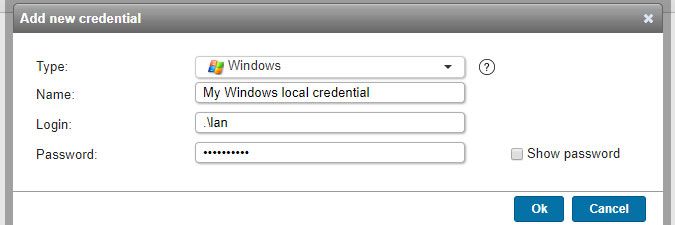
Windows credentials
- Used for scanning: Windows computers and users.
- Must have: administrative permissions on your computers and, for scanning domain computers and users, read-only access to Active Directory. A domain admin can be used to scan a domain, but has more permissions than required. More info on Windows domain scanning requirements can be found in this knowledge base article and more info on Windows workgroup scanning requirements can be found in this knowledge base article.
- Name: custom name you can assign to the credential.
- Login: a down-level logon name like NetBIOS domain name\username (domain credentials) or a user principal name (UPN) like username@yourdomain.local (domain credentials) or .\username (local credentials) or username@outlook.com (Microsoft accounts).
- Password: your user account's password.
Mapping scanning credentials
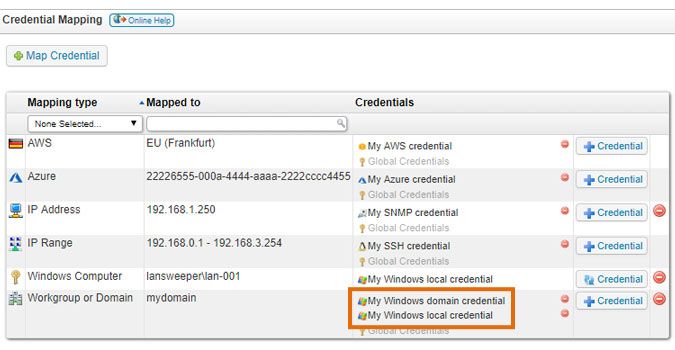
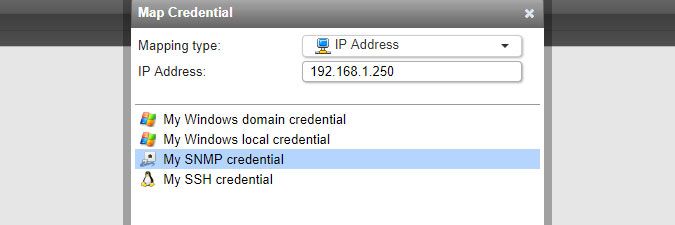
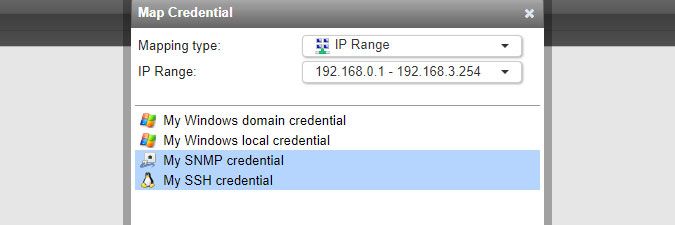
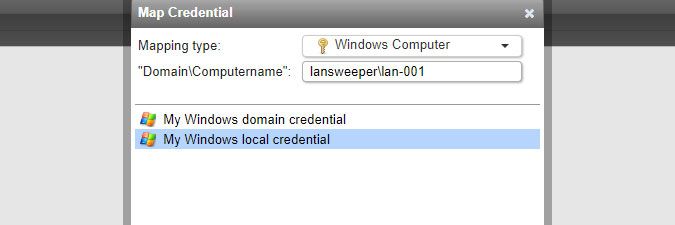
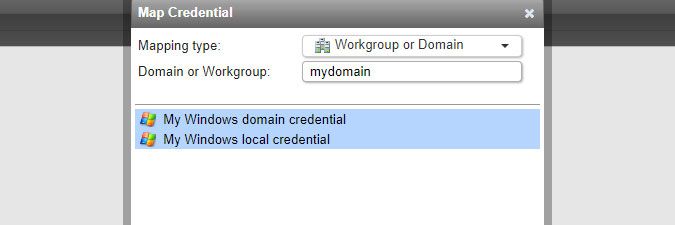
To map a credential, click the Map Credential button in the Scanning > Scanning Credentials section of the web console. You can select multiple credentials at once.
Credentials are tried in the order you see them. In the example below, Lansweeper will first try the Window domain credential and then the local credential. You can change the order in which credentials are tried by grabbing (left-click and hold) a credential in the Credentials column and dragging it to a new position.
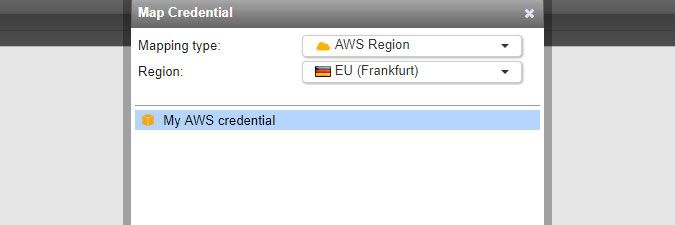
An AWS region
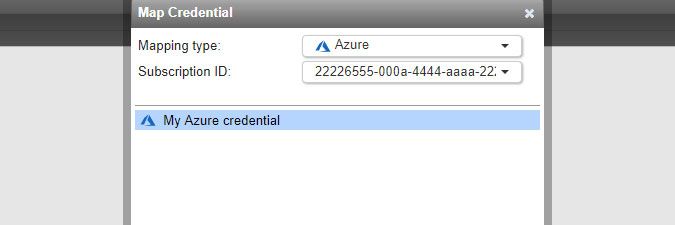
An Azure subscription ID
An IP address
An IP range
An individual Windows computer
NetBIOS domain name\NetBIOS computer name or workgroup name\NetBIOS computer name.A domain or workgroup
Was this post helpful? Select Yes or No below!
Did you have a similar issue and a different solution? Or did you not find the information you needed? Create a post in our Community Forum for your fellow IT Heroes!
More questions? Browse our Quick Tech Solutions.
New to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try NowNew to Lansweeper?
Try Lansweeper For Free
Experience Lansweeper with your own data. Sign up now for a 14-day free trial.
Try Now