Operational technology (OT) is everywhere – in manufacturing facilities, industrial complexes, stores, and construction sites. Not only does it power a range of industrial and operational systems, but it also works behind the scenes at organizations in nearly every industry, keeping the lights on and the water running – and it runs 24/7.
Examples of Operational Technology include:
- PLC: Programmable Logic Controllers
- SCADA: Supervisory control and data acquisition
- DCS: Distributed Control Systems
- CNC: Computer Numerical Control Systems, including computerized machine tools
- BMS/BAS: Building Management and Building Automation Systems
- Lighting controls both for internal and external applications
- Energy monitoring, security, and safety systems for the built environment
In the past, much of the operational technology in an organization was isolated from the corporate network. It used proprietary control protocols, a proprietary OS, and specialized hardware to function. All that’s changed. Today, operational technology is often bridged into corporate networks using common internet protocols, and much of it consists of general-purpose hardware running mainstream operating systems. The IT and OT convergence has introduced increased risk that cannot be ignored.
Operational Technology Cybersecurity
Incidents such as Stuxnet and the Colonial pipeline highlighted the importance of Operational Technology Cybersecurity – the Stuxnet worm infected over 20,000 devices in 14 Iranian nuclear facilities and ruined around 900 centrifuges, while the attack on the Colonial pipeline resulted in $90 million in financial losses. Meanwhile, evolving cybersecurity regulations are putting pressure on cybersecurity professionals to ensure compliance across the entire technology estate – operational technology included.
With all that’s at stake, technologies and processes for increasing Operational Technology visibility are essential – you can’t protect, update or manage devices you don’t know you have. Unfortunately, those responsible for keeping all of the Operational Technology up and running often don’t have complete visibility into their hardware and software – and therefore cannot maintain, update or replace it when needed. Decades-old technology can linger in the OT environment, outdated and unprotected. Not only can outages impact business continuity and cause financial losses, but these devices are also sitting ducks for cybercriminals…
Operational Technology Asset Management
With Operational Technology Asset Management – a complete inventory of all operational technology assets, organizations can map possible attack vectors to secure their business better and create up-to-date, accurate, and in-depth reporting on all technology assets in the business.
The goal is to create a list of all OT assets and keep it up to date, reducing workload through preventive maintenance and protecting assets through the timely discovery of asset vulnerabilities. Devices that receive updates and maintenance also run more efficiently and reduce the risk of production outages. But more often than should be the case, a full overview of all devices an organization has under management is lacking and companies don’t have the necessary staff to service them properly. Deploying an automated solution to create an always up-to-date list of all OT assets would go a long way in helping organizations tackle this challenge.
Creating an Automated OT Asset Inventory by deploying an OT Scanner
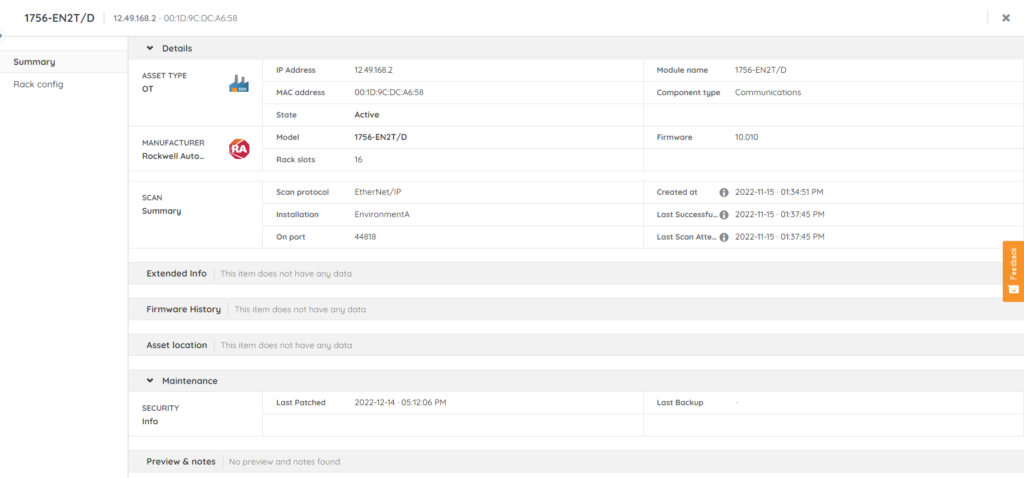
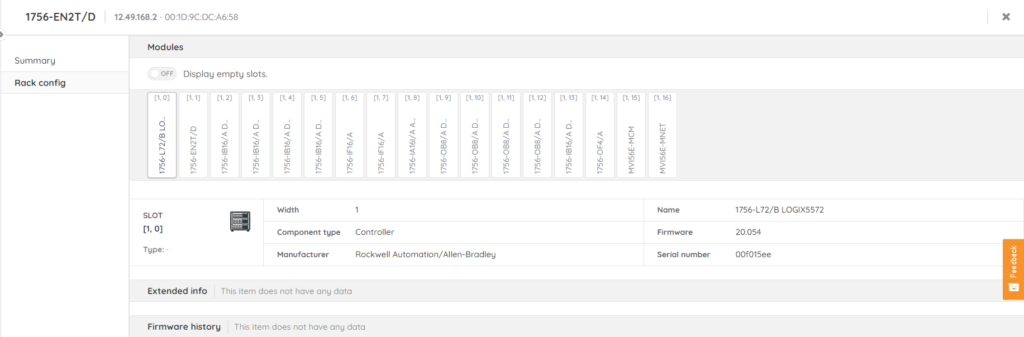
Lansweeper’s OT Discovery solution enables organizations to create up-to-date, accurate, and in-depth inventory & vulnerability reports on their OT assets. Lansweeper relies on Selective Probing for a deeper understanding of the OT environment and all devices on that network. To understand why this is important, let’s take a look at the various types of scanning technologies available:
Passive scanning
Passive Scanning records device information when the device activates to communicate with the network or other devices. In other words, it simply listens for devices that emit a signal and then logs them. While the most critical assets on your production line – and those that are used the most – will be recorded, this method omits devices that don’t use the network to communicate. On top of that, passive scanning is limited to capturing the traffic being communicated over the network by the device. If some essential data, like firmware version, for instance, is not part of the package you will not capture it. Another disadvantage of this method is that it’s architecture-dependent and not centrally managed, so if it’s not perfectly configured, you’ll miss out on traffic and won’t have complete network visibility.
Active scanning
Active Scanning proactively pings and contacts devices to get hardware and software information. Anything connected to the network is discovered – even Shadow IT, idle devices, and rogue devices that only touch the network briefly. However, it creates additional network load and when improperly used can cause failed package delivery, produce communication errors, and can ultimately cause disruption of OT Devices & networks. Active scanning is more suitable for IT systems, which are often more robust than OT devices.
Selective Probing
Specifically for scanning OT Devices, Lansweeper has developed a new way of scanning – Selective Probing, which provides a middle ground ideal for discovering Operational Technology assets. It creates a perfect balance between risk-free, passively recording communication and the richness of active scanning. With Selective Probing, the most important assets of your production line are recorded alongside devices that don’t communicate over the network.
It’s like active scanning, but more careful. Selective Probing can query multiple devices in the network, but a single device will only be queried serially, with sufficient time between queries and only with validated, safe communication.
Lansweeper uses Selective Probing to identify OT devices from Siemens, Rockwell Automation, Mitsubishi Electric, Schneider Electric,… leveraging unique OT protocols, to provide a complete and accurate inventory of all OT devices across the business. With this information on-hand, operational technology security professionals can easily plan and manage updates and maintenance, remediate any vulnerabilities, and have complete visibility of the expanding and increasingly diverse technology landscape.
Ready to learn more about Lansweeper OT?
DOWNLOAD OT SCANNERFor a complete understanding of the level of visibility Lansweeper’s new OT Discovery tool surfaces, watch the Lansweeper OT webinar. If you want to get started directly, it’s easy to download and setup the new Lansweeper for OT installer.